What Is the Plan?
A Phase-by-Phase Analysis of the Q Operation Through the Lens of Fifth Generation Warfare
Disclaimer (Read This First)
This article represents my analytical model based on military and law-enforcement operational planning, intelligence tradecraft study, Fifth Generation Warfare theory, social psychology, human behavioral analysis, and lived experience in complex investigations. It does not claim classified access or inside command authority. What follows is a structured theory of operations - intended to educate, prepare, and strengthen the reader for the modern information battlespace.
Introduction: Understanding the War You’re Already In
Most people still think war announces itself.
They expect declarations, uniforms, explosions, and clearly defined enemies. That expectation is itself a vulnerability, because the most effective wars no longer look like wars at all.
We are living inside Fifth Generation Warfare: conflict waged not over territory, but over perception, belief, morale, identity, and meaning. In this battlespace, the primary targets are civilian populations, and the decisive weapon is information - filtered, distorted, weaponized, or withheld.
My perspective on this war is not theoretical.
It is shaped by years of military and law-enforcement experience, including combat, operational planning fourteen years in policing within a high-crime, gang-dominated environment - serving not only as a street officer, but as a detective working homicides, undercover operations, gang investigations, and priority violent crime. I was also responsible for strategic planning and coordination of large-scale domestic operations, often involving multiple agencies with overlapping jurisdictions and competing incentives.
That experience matters, because modern information warfare behaves far more like organized crime and long-term conspiracy cases than like conventional battlefields.
It involves:
Compartmentalization
Cutouts and plausible deniability
Narrative laundering
Financial pipelines and shell structures
Controlled leaks and psychological pressure
Populations treated as targets rather than stakeholders
These are not abstract theories. They are familiar patterns to anyone who has dismantled criminal networks, built RICO-style cases, or coordinated investigations where truth had to be inferred from behavior, not statements.
At the strategic level, institutions such as the CIA, NSA, the FBI, USAID, the National Endowment for Democracy (NED), NATO, and even the British Crown do not operate merely as neutral bureaucracies. They function, often in coordination, as narrative managers, influence brokers, and continuity mechanisms for a post-sovereign global order.
Their power does not primarily rest in uniforms or weapons.
It rests in control of information flow, financial leverage, institutional inertia, and psychological compliance.
This is the environment in which the “Q” Operation must be evaluated.
Not as a political movement.
Not as an internet phenomenon.
Not as a belief system.
But as a counter-information and counter-influence operation, designed to disrupt, expose, and eventually collapse an entrenched system of narrative control - using the population itself as the decisive force.
The mistake both critics and uncritical followers make is the same: they judge Q by emotional satisfaction, missed predictions, or symbolic expectations. That is not how operations - criminal, intelligence, or military - are assessed.
You assess an operation by outcomes:
Did it alter behavior?
Did it fracture trust in hostile institutions?
Did it force people to validate information instead of consuming it?
Did it expose the mechanics of power rather than just its personalities?
Did it shift responsibility from centralized authority to decentralized action?
This article exists to answer one question…calmly, systematically, and without emotional manipulation:
What is the Plan?
Not as a slogan.
Not as faith.
But as a phase-based operational theory, grounded in how real investigations, influence campaigns, and long-duration operations unfold.
What follows is a 17-phase doctrine, a campaign map, analyzed through the combined lenses of:
Military operational planning
Law-enforcement and domestic strategic operations
Intelligence community tradecraft
Fifth Generation Warfare theory
Social psychology and human behavioral modeling
This is written for two audiences simultaneously:
For the skeptic: Structure, logic, sequencing, and cause-and-effect -without requiring belief or allegiance.
For the Q-aware: Discipline, grounding, and clarity -separating signal from noise, strategy from mythology.
By the end of this series, you will be equipped to:
Recognize information weapons in real time
Understand why destabilizing events are sometimes allowed to unfold
Identify controlled opposition and psychological traps
Maintain morale under sustained narrative pressure
Interpret unfolding events without panic, hero worship, or despair
This is not about waiting to be saved.
In Fifth Generation Warfare, the population is the decisive terrain.
And morale…disciplined, informed, resilient morale…is the most powerful weapon available.
What follows is not a promise.
It is an operational map.
Table of Contents: The 17-Phase Operational Doctrine
Phase 1: Delegitimizing the Mainstream Media: Breaking the Propaganda Monopoly
Phase 2: Creating an Alternative Information Pathway: Operation Q Defined
Phase 3: Training the Population: 5GW Literacy and Citizen Investigators
Phase 4: Exposing the Continuity Plan: Managed Democracy and the 16-Year Design
Phase 5: Election Awareness Through Consequence: Movie I and Movie II
Phase 6: The Responsibility Shift: “We The People” as the Center of Gravity
Phase 7: Electoral Overwhelm: Winning by Scale to Break Systemic Fraud
Phase 8: Financial Exposure: USAID, NED, NGOs, and Laundered Power
Phase 9: Controlled Opposition Cleanup: RINOs, False MAGA, and Psy-Ops Actors
Phase 10: Legal Warfare: RICO Pathways and Indictment Sequencing
Phase 11: Election System Lock-In: Securing the Midterms and Beyond
Phase 12: The Sovereign Alliance: Redefining Enemies and Exposing NATO Control
Phase 13: Neutralizing Chaos Operations: Civil War, Religious War, Terror Theater
Phase 14: National Unification: Post-Exposure Psychological Realignment
Phase 15: The Final Confrontation: Institutional Collapse (Late 2026–Early 2027)
Phase 16: Global Sovereignty Restoration: Trials, Borders, and Legitimate States
Phase 17: The Golden Age: Transparency, Accountability, and Civilizational Renewal
Phase 1: Delegitimizing the Mainstream Media
Breaking the Propaganda Monopoly
Phase 1 is not optional.
It is not political.
It is foundational.
In every modern influence campaign, whether conducted by a foreign intelligence service, a domestic political machine, or a transnational power bloc, the first and most important objective is control of the information environment. Whoever controls what people believe is real, controls how they behave. Whoever controls behavior controls outcomes.
From a military, intelligence, and law-enforcement perspective, Mainstream Media is not a neutral observer. It functions as a force multiplier, a delivery system for narratives that shape public perception, legitimize authority, protect institutions, and discredit threats to power.
If you do not neutralize this weapon, nothing else can proceed.
Media as a Weapon System (Not a Profession)
In conventional war, you identify:
Command and control
Logistics
Communications
Morale infrastructure
In Fifth Generation Warfare, media replaces artillery.
Legacy outlets do not simply report events; they frame reality. Framing determines:
What is considered possible
What is considered acceptable
Who is considered credible
What questions are permitted and which are treated as dangerous
From an investigative standpoint, this mirrors organized crime dynamics:
Repetition replaces evidence
Authority replaces proof
Dissent is treated as guilt
Silence is used as suppression
This is not accidental.
Institutions such as the CIA and NSA have long understood that information dominance is more efficient than force. Domestic counterparts, including the FBI, operate within a system where media partnership can shape investigations, outcomes, and public consent long before facts are adjudicated.
From a law-enforcement lens, this is familiar territory.
You don’t need to jail everyone if you can:
Control the narrative
Pre-label suspects
Pressure witnesses
Shape public expectation of guilt or innocence
Media does for institutions what public affairs officers do for agencies, except with far less accountability.
Why Delegitimization Had to Come First
Before the public could be shown corruption, fraud, or institutional capture, they had to be taught not to reflexively trust the messenger.
This is basic counter-intelligence logic.
If a population trusts the adversary’s communications system, any exposure you introduce will be rejected, regardless of evidence. The immune system of belief will attack the truth as a foreign body.
So Phase 1 was designed to accomplish one goal:
Break the spell of authority.
Not destroy journalism.
Not silence reporters.
But collapse blind trust.
President Trump’s repeated use of “Fake News” was not rhetorical frustration. It was a psychological wedge. The phrase was deliberately blunt, repetitive, and emotionally jarring, because its purpose was not persuasion. It was disruption.
From a policing standpoint, this is the equivalent of introducing reasonable doubt before a jury ever hears evidence.
Once doubt exists, control is broken.
Pattern Recognition Over Proof
Critics often say, “Calling the media fake isn’t evidence.”
They’re correct and they miss the point.
Phase 1 was not about proving individual lies.
It was about teaching pattern recognition.
In investigations, patterns matter more than statements:
Who gets protected?
Who gets attacked?
What stories are synchronized?
What topics are ignored across outlets simultaneously?
When narratives change, who benefits?
When the same talking points appear across supposedly competing networks, skepticism becomes unavoidable.
This is how detectives think.
This is how intelligence analysts think.
This is how populations must think to survive information warfare.
Phase 1 trained millions of people, many unknowingly, to stop asking, “Is this true?” and start asking:
“Who needs me to believe this and why?”
That single shift breaks propaganda permanently.
Delegitimization Without Replacement Is Chaos
Here is where most revolutions fail.
If you destroy trust in an authority without providing an alternative framework, you get:
Cynicism
Apathy
Radicalization
Nihilism
Phase 1 alone would have been irresponsible.
That is why Phase 1 was never meant to stand on its own.
Its purpose was to clear the terrain, to create an information vacuum that would later be filled by a decentralized alternative. That alternative is addressed in Phase 2.
But the sequencing matters:
Trust must collapse first
Curiosity must replace obedience
Investigation must replace consumption
From a morale perspective, this phase is psychologically destabilizing, but necessary. Every long-term investigation has a moment where the comfortable story collapses and uncertainty takes over.
Good operators don’t panic at that moment.
They lean in.
Why This Phase Took Years
Many expected the media collapse to be immediate. That expectation reveals a misunderstanding of human behavior.
Belief systems tied to identity do not collapse overnight. They degrade incrementally:
First through doubt
Then through contradiction
Then through fatigue
Finally through disbelief
Phase 1 had to be slow enough to avoid mass rejection, but persistent enough to be irreversible.
By the time censorship intensified, deplatforming accelerated, and coordinated messaging became obvious, the work was already done.
People didn’t need to be told the media was compromised.
They felt it.
And in psychological warfare, felt truth is more powerful than factual truth.
Phase 1 End State
Phase 1 is complete when:
Media authority is no longer absolute
Official narratives are questioned by default
Trust shifts from institutions to independent verification
The population becomes curious instead of compliant
At that point, the propaganda weapon still exists, but it no longer dominates the battlefield.
The monopoly is broken.
Only then can Phase 2 begin.
Key Takeaway
Phase 1 was not about anger.
It was not about clicks.
It was not about politics.
It was about freeing the human mind from reflexive obedience.
You cannot teach people to think critically while they still believe authority equals truth.
You must first remove the blindfold.
Next:
Phase 2 - Creating an Alternative Information Pathway
Why Operation Q did not give answers, but instead built investigators.
Phase 2: Creating an Alternative Information Pathway
Operation Q Defined
Phase 1 fractured trust in the legacy information system. That alone was necessary, but insufficient.
Every investigator, commander, or task-force lead understands the danger of what comes next: the vacuum.
When an entrenched structure collapses -whether it’s a criminal organization, a corrupt institution, or a dominant narrative…something will replace it. If that replacement is unmanaged, the result is not truth. It is chaos, rumor, opportunism, and further psychological destabilization.
Phase 2 exists to prevent that outcome.
Its objective was not to replace Mainstream Media with another centralized authority. That would simply recreate the same dependency model under a different name. Instead, Phase 2 was designed to change the population’s relationship with information itself.
This distinction is critical.
Why an Alternative Pathway Was Required
Legacy media did more than deliver news. It provided:
Narrative coherence
Psychological reassurance through authority
A shared sense of “what matters”
Once delegitimized, millions of people were left disoriented. From a law-enforcement perspective, this mirrors what happens when a dominant criminal group is dismantled without stabilizing the environment: confusion spreads, trust collapses, and opportunists rush in.
Phase 2 was designed to absorb and stabilize that disorientation, not by issuing conclusions, but by introducing a new method of engagement.
The goal was not belief.
The goal was participation.
Operation Q Was Not a News Source
This is the most important misunderstanding to correct.
Operation Q was never intended to function as:
An intelligence leak
A whistleblower channel
A replacement press outlet
Those models centralize authority and encourage passivity. They tell people what to think, not how to think. That is exactly the vulnerability exploited by propaganda systems.
Instead, Q functioned as a cognitive training mechanism.
From a military and law-enforcement lens, it resembled:
A partially redacted case file
An investigative lead sheet
A briefing stripped of conclusions
Information was intentionally incomplete. Context had to be earned. Meaning had to be constructed, not consumed.
This was not accidental. It was doctrinal.
The Mocking Bird Main Stream Media wanted President Trump to denounce “QAnon (No such thing, there is Q and there are Anons)”. He refused to denounce Q, instead he complimented them.
Primary Source Confirmation: Q Post #96 (One of my favorites)
One of the clearest confirmations of Phase 2’s intent appears early in the operation itself.
In Q Post #96 (November 5, 2017), the stated purpose is explicit:
“Amazing how things make sense once you are asked a question. That’s the entire point of this operation.”
This sentence alone dismantles the claim that Q existed to dictate belief. In investigative training, questions activate cognition; answers create dependency. This is the Socratic method, not indoctrination.
The post continues:
“It’s up to you all to collect, archive (safely), and distribute…”
This is tasking language. It assigns responsibility outward, not upward. The audience is not treated as followers waiting for instruction, but as participants expected to engage, preserve information, and share it independently.
From an operational standpoint, this is a decentralization strategy. Authority is not reinforced, it is dissolved.
The population is not told what the truth is.
They are told to go find it.
Decentralization as a Strategic Weapon
Centralized truth is easy to attack.
Discredit the source and the narrative collapses.
Decentralized investigation is resilient. When thousands of independent actors pursue parallel lines of inquiry, without formal coordination, control becomes impossible. No single failure discredits the whole. No single censor can shut it down.
This mirrors effective task-force design in law enforcement:
No single point of failure
Compartmentalized effort
Independent corroboration
Emergent pattern recognition
Operation Q distributed the investigative burden across the population itself. That was not a flaw. It was the feature.
Why Ambiguity Was Intentional
Ambiguity frustrates people who expect instruction. It empowers people who can operate under uncertainty.
From a behavioral psychology standpoint:
Certainty creates passivity
Ambiguity creates engagement
Operator’s never divulge.
Less than 10 can confirm me.
By refusing to provide finished answers, Phase 2 forced individuals to confront their own cognitive habits:
Do they seek validation or understanding?
Do they chase emotional payoff or disciplined inquiry?
Do they verify or merely repeat?
This is how analysts are identified and developed.
Those who required constant certainty burned out.
Those who adapted became more capable over time.
That sorting process is unavoidable in any serious operation.
Why There Were No Direct Calls to Action
Phase 2 deliberately avoided mass mobilization, commands, or operational directives.
This was not hesitation. It was restraint.
From a legal, intelligence, and law-enforcement perspective, premature action would have:
Provided justification for suppression
Triggered counter-operations
Fractured legitimacy
Converted observers into liabilities
Instead, the focus remained on mental mobilization.
You do not rush a population into action before it understands the terrain.
You train it first.
The Psychological Shift Achieved
By the end of Phase 2, something subtle but irreversible had occurred.
A significant portion of the population no longer:
Deferred automatically to authority
Consumed information passively
Accepted narratives without scrutiny
They began to:
Ask better questions
Compare competing explanations
Seek original sources
Recognize emotional manipulation
This is not awakening rhetoric.
It is behavioral reconditioning.
From an investigative standpoint, it is the moment a witness stops parroting a story and begins speaking independently. Once that happens, regression is unlikely.
Phase 2 End State
Phase 2 is complete when:
Authority no longer monopolizes truth
Information flows horizontally, not vertically
Curiosity replaces fear as the dominant driver
The population becomes cognitively engaged
At that point, the battlefield has fundamentally changed.
The people are no longer an audience.
They are participants.
Key Takeaway
Phase 1 broke blind trust.
Phase 2 rebuilt cognitive capability.
Operation Q did not exist to give answers.
It existed to teach people how to arrive at them, independently, resiliently, and without reliance on centralized authority.
That is how information warfare is won.
Next:
Phase 3 – Training the Population in Fifth Generation Warfare
How pattern recognition, psychological resilience, and informal education transformed civilians into information-aware operators.
Transition: From Investigation to Warfare Literacy
Phase 2 succeeded in doing exactly what it was designed to do.
It broke the habit of passive consumption and replaced it with active inquiry. People stopped waiting for permission to think. They began questioning narratives, comparing sources, and recognizing inconsistencies on their own.
But investigation alone is not enough.
Anyone who has worked complex, long-term cases understands this limitation. Without a governing framework, investigators:
Chase false patterns
Over-interpret coincidence
Burn out emotionally
Confuse volume of information with understanding
Raw curiosity, without doctrine, creates noise.
At a certain point, the population accumulated questions faster than it could process them. Information volume increased, but clarity did not. This was not a failure of the operation, it was a predictable inflection point.
In any serious operation, this is where training begins.
Phase 3 marks that transition.
The operation moves from asking questions to understanding the battlespace itself. It introduces Fifth Generation Warfare not as an abstract theory, but as a practical operating model for recognizing psychological pressure, narrative manipulation, morale warfare, and population shaping in real time.
Phase 2 created investigators.
Phase 3 begins the process of creating information-aware operators.
Phase 3: Training the Population in Fifth Generation Warfare
From Curiosity to Cognitive Discipline
Every war has a moment where raw enthusiasm must give way to training.
In conventional conflict, you don’t hand someone a weapon and call them a soldier. You teach them doctrine, rules of engagement, threat identification, and discipline under stress. Information warfare is no different. The strategies & tactics of war still apply in the digital battlefield.
Phase 3 exists because untrained awareness is dangerous to the individual and to the operation.
Once people begin to recognize deception, they also become vulnerable to:
Overreaction
Paranoia
Pattern obsession
Emotional manipulation from alternative actors
This phase was designed to prevent that.
What Fifth Generation Warfare Actually Is
Fifth Generation Warfare (5GW) is not about bullets or borders. It is about shaping perception at scale.
Its defining characteristics include:
Psychological pressure instead of kinetic force
Narrative dominance instead of territorial control
Population behavior as the primary objective
Morale as a weapon system
In 5GW, the target is not the enemy’s army.
It is the enemy’s population.
This is why modern conflicts focus on:
Media saturation
Emotional amplification
Identity fragmentation
Moral exhaustion - How many times have you heard or read “I am tired of seeing this or hearing about this”
And this is why populations that do not understand 5GW are easily steered, even while believing they are informed.
Why Training Had to Be Informal and Distributed
Formal education systems are slow, hierarchical, and easily captured.
Phase 3 could not rely on:
Universities
Official military schools
Government training pipelines
Those institutions are constrained by politics, funding, and narrative control.
Instead, 5GW concepts were introduced informally, through:
Independent researchers/anons
Decentralized communities/social media
Long-form discussions/podcast
Pattern-based analysis
Figures like General Michael Flynn and Boone Cutler helped articulate these ideas publicly, not as classified doctrine, but as conceptual literacy.
This was not about teaching secrets.
It was about teaching how to see.
Core Skills Phase 3 Was Designed to Develop
Phase 3 focused on developing specific cognitive disciplines:
1. Pattern Recognition Without Obsession
Operators learn to distinguish between:
Meaningful coordination
Coincidence
Deliberate distraction
Not every pattern is real. Not every signal matters.
2. Emotional Regulation Under Narrative Pressure
Fear, anger, and moral outrage are tools in 5GW. Training teaches:
Delay of reaction
Emotional self-monitoring
Resistance to manufactured urgency
3. Understanding Psychological Operations (PsyOps)
Readers begin to recognize:
How narratives are framed
Why certain language is repeated
How moral binaries are used to suppress thought
4. Morale as a Strategic Asset
In 5GW, morale is not a byproduct - it is a weapon.
Panic weakens populations
Hopelessness paralyzes them
Calm confidence makes them uncontrollable
Phase 3 reframed morale from “feeling good” to operational stability.
Why Mistakes Were Inevitable and Useful
From a training perspective, confusion was not an accident.
Early in Phase 3, many people:
Over-interpreted signals
Assigned certainty where none existed
Fell for counter-narratives and grifters
This mirrors every training pipeline.
You learn who can:
Self-correct
Accept uncertainty
Adjust models when facts change
And who cannot.
Operations do not require universal participation.
They require capable participants.
The Psychological Shift Achieved
By the end of Phase 3, a subset of the population had developed something rare:
Cognitive resilience.
They could:
Observe without reacting
Analyze without spiraling
Hold uncertainty without fear
Wait without disengaging
This is the mindset required to survive long-duration psychological conflict.
It is also the mindset legacy systems cannot control.
Phase 3 End State
Phase 3 is complete when:
The population understands it is under psychological attack
Emotional manipulation loses effectiveness
Narrative swings fail to produce panic
Morale becomes internally generated, not externally supplied
At this point, the population is no longer just aware.
It is trained.
Key Takeaway
Phase 1 broke blind trust.
Phase 2 created investigators.
Phase 3 built discipline.
This is where curiosity became capability.
Only after this point could the operation safely proceed into exposure, legal warfare, and institutional confrontation, without the population becoming a liability.
Next:
Phase 4 – Exposing the Long-Term Continuity Plan
How managed democracy, institutional capture, and the illusion of choice were revealed and why timing mattered.
Phase 4: Exposing the Long-Term Continuity Plan
Managed Democracy, Institutional Capture, and the Illusion of Choice
Phase 4 is where the operation transitions from training the mind to revealing the design.
Up to this point, the population had been prepared:
Trust in legacy authority had been broken (Phase 1)
Citizens had been activated as investigators (Phase 2)
Psychological discipline had been introduced (Phase 3)
Now came the moment where people could be shown what those tools were actually for.
Phase 4 answers a question that sits beneath nearly every modern political debate:
If elections matter, why do outcomes feel inevitable?
The answer is not fraud alone.
The answer is continuity.
Managed Democracy: Control Without Cancellation
Managed democracy does not eliminate elections. It neutralizes them.
In a managed democratic system:
Voting continues
Parties rotate
Media debates intensify
Institutions remain untouched
The population believes it is choosing direction, while the range of acceptable outcomes is pre-approved.
From a law-enforcement and intelligence perspective, this is familiar territory. Large criminal or corrupt enterprises survive not by overt control, but by managing exposure, sequencing leadership, and insulating command structures from disruption.
The illusion of choice is more stable than open force.
The Continuity Model: Conditioning Before Execution
What later became known as the “16-year plan” was not a slogan. It was a logical continuity model.
From an operational standpoint, long-term control requires two distinct phases:
Conditioning the environment
Executing irreversible change
The first eight years were not designed to end the United States. They were designed to weaken it internally.
Under the administration of Barack Obama, a series of conditions emerged that align with classic internal destabilization doctrine:
Erosion of trust between the population and law enforcement
Normalization of ideological street movements and civil unrest
Expansion of border permissiveness
Degradation of military readiness and morale
Placement of ideologically aligned operators within permanent bureaucratic positions
Whether one attributes these outcomes to intent, ideology, or institutional capture is ultimately secondary. In operational analysis, effects matter more than motives.
The net result was a country less cohesive, less resilient, and more psychologically divided, while still appearing stable on the surface.
This was conditioning, not execution.
Why Hillary Clinton Mattered Strategically
The second phase of the continuity model required consolidation.
Hillary Clinton was not simply a candidate. She represented assured continuity with escalation.
From an operational perspective, the next eight years were projected to:
Convert bureaucratic capture into permanent administrative control
Neutralize remaining institutional resistance
Expand international conflict obligations
Restrict civilian self-defense and political dissent
Collapse economic independence into managed dependency
In this model, elections did not disappear. They became procedural theater, a legitimizing ritual rather than a mechanism of change.
This is why the idea of inevitability was so aggressively promoted leading into 2016.
Why Trump Was an Existential Disruption
Donald Trump was not dangerous to the system because of his personality.
He was dangerous because he violated sequencing.
He did not come from:
Approved political grooming pipelines
Intelligence-adjacent vetting processes
Consensus-driven global governance circles
From an operational standpoint, Trump represented an uncontrolled variable introduced at the worst possible time - between conditioning and execution.
That is why the reaction to his 2016 victory was immediate, coordinated, and disproportionate.
In investigative terms, it resembled an outsider walking into a protected enterprise and refusing:
Co-optation
Intimidation
Narrative compliance
The continuity model could no longer proceed cleanly.
Exposure Through Disruption, Not Explanation
Phase 4 could not be delivered as a lecture.
You cannot simply tell a population:
“Your elections have become theater.”
That truth must be demonstrated, not declared.
Instead, exposure occurred through institutional behavior under stress:
Who was protected versus relentlessly pursued
Which investigations never materialized
Where rules applied selectively
How media narratives synchronized instantly
From a law-enforcement perspective, corruption is rarely proven by confession. It is proven by patterned exemption.
People began to see that accountability was not evenly distributed.
The Psychological Breakpoint
At a certain point, a critical mass of the population reached a realization:
If voting alone determines outcomes, why does nothing fundamentally change?
This moment is dangerous.
Without preparation, it leads to:
Apathy
Extremism
National fracture
But because Phases 1–3 had already built information literacy and psychological discipline, the effect was different.
Instead of despair, it produced clarity.
From Partisan Conflict to Structural Awareness
Phase 4 marks the shift away from partisan explanation toward structural understanding.
People began to recognize:
Power is not located where it is advertised
Institutions outlast elected officials
Continuity is enforced administratively, not democratically
This is not cynicism.
It is operational realism.
In complex investigations, you stop asking “Who is lying?” and start asking:
“Who is insulated, no matter who wins?”
That question permanently changes perception.
Phase 4 End State
Phase 4 is complete when:
The illusion of unrestricted electoral choice collapses
Institutional behavior is judged over political rhetoric
Continuity becomes visible as a system
Disruption is no longer feared, but understood as necessary
At this point, the population is ready for the next lesson.
Not theory.
Consequence.
Key Takeaway
Phase 4 was not about convincing people the system failed.
It was about showing them why the system required control to survive.
Once that understanding takes root, exposure is inevitable.
Next:
Phase 5 – Election Awareness Through Consequence
Why lived experience…not argument…completed the lesson.
Phase 5: Election Awareness Through Consequence
“Movie I” and “Movie II” Why Exposure Had to Be Experienced, Not Announced
Phase 5 is where the operation stops trying to convince and starts trying to convert perception into certainty.
By now, the reader has the prerequisite foundation:
Phase 1: The propaganda monopoly is fractured.
Phase 2: The citizen becomes an investigator, not a consumer.
Phase 3: The investigator gains 5GW discipline and emotional control.
Phase 4: The public is shown the architecture of continuity, managed democracy and the illusion of choice.
Now comes the hard truth that every homicide detective, counterintel analyst, and operational planner learns early:
Some realities cannot be “explained” into acceptance. They must be lived into recognition.
People can argue with claims.
They can dismiss reports.
They can rationalize contradictions.
But they cannot unsee consequence.
Phase 5 is built around that principle.
Primary-Source: The “Show Them” Doctrine (Q Posts #4908 and #4024)
Two posts summarize the core doctrine:
“Sometimes you can’t TELL the public the truth. YOU MUST SHOW THEM.”
“A deeply entrenched enemy who controls the vast majority of communications is only defeated by… Game theory.”
Read those as operational statements, not slogans.
In law enforcement terms: you can’t lecture a jury into certainty- you build a case so clear that denial becomes irrational.
In intelligence terms: you don’t defeat a narrative machine by arguing; you defeat it by forcing it to reveal itself in the real world.
In 5GW terms: you break the spell by creating experiential proof, the kind that bypasses propaganda filters.
That’s Phase 5.
What Phase 5 Actually Does
Phase 5 has four strategic objectives:
1) Convert suspicion into recognition
The public moves from “I think something’s wrong” to:
“I understand the mechanism, and I can see it operating.”
2) Make denial psychologically expensive
When reality contradicts official messaging continuously, the psychological cost of maintaining the lie becomes too high.
3) Remove the crutch of “authority validation”
Phase 5 forces people to stop waiting for institutions to confirm institutional corruption.
4) Produce WILL
As Q Post #4908 states in essence: once people see the truth in lived consequence, they find the will to change.
Will is not produced by information alone…it’s produced by pain + clarity.
Why This Phase Had to Be a “Movie”
The “movie” framing matters because it communicates something important:
In 5GW, perception is shaped through narrative sequencing
Sequencing creates learning
Learning creates mass behavioral shift
A movie isn’t just content. It’s a structured emotional and cognitive journey.
Phase 5 is the journey where:
the “illusion of choice” becomes visible,
and the system’s true nature can no longer be rationalized away.
Movie I: Trump’s First Term as a Demonstration of System Defense
Movie I is not primarily about policy outcomes.
It’s about system behavior under disruption.
From an operational viewpoint, Trump’s first term serves as a stress test exposing the regime’s immune response:
Coordinated media framing and synchronization
Relentless delegitimization of the elected executive
Permanent bureaucracy friction and sabotage dynamics
Institutional “refusal to comply” behavior masked as professionalism
Narrative warfare replacing normal governance
For skeptics: you don’t even have to agree on motives to see the pattern.
When a system reacts with this level of unified hostility, it signals a deeper truth:
The threat was not ideological. The threat was disruption of continuity.
This is the same way you detect a protected criminal structure.
You watch who panics, who closes ranks, who suddenly shares the same talking points, who becomes untouchable, and who becomes the designated enemy.
Movie I teaches the public a crucial lesson:
There is a governing layer that does not consent to electoral disruption.
The Inflection Point: From “Rigged Narratives” to “Rigged Outcomes”
Phase 5 is where the question evolves:
Phase 1 question: “Is the media lying?”
Phase 2 question: “How do I find truth without them?”
Phase 3 question: “What is the battlefield doing to my mind?”
Phase 4 question: “Is there a continuity plan?”
Phase 5 question: “If the system must be protected, what happens when voters disrupt it?”
This is where election awareness becomes unavoidable, not as a partisan claim, but as a structural suspicion:
If continuity is the priority, then elections must either be managed… or neutralized.
That’s the logic Phase 5 forces into the open.
Movie II: The Consequence Demonstration
Movie II is where Phase 4’s architecture becomes tangible.
Rather than trying to persuade the public with arguments, Movie II functions as experiential instruction:
“This is what continuity looks like when uninterrupted.”
“This is what institutional capture produces when unchallenged.”
“This is what happens when the population is governed against its will while being told it is ‘normal.’”
In this theory, this period becomes the “show them” segment, because regardless of a person’s media diet, the public is forced to confront system outputs:
Border stress and loss of operational control
Expansion of trafficking networks (a known byproduct of border instability)
Public confidence erosion in institutions
Economic pressure and dependency incentives
Cultural destabilization and morale degradation
Increased narrative warfare to manage perceptions of decline
The key is not arguing each item endlessly, it’s recognizing the operational pattern:
A population under 5GW pressure experiences confusion, exhaustion, division, and learned helplessness.
This is the moral and psychological battlefield.
And it is intentional in this model: because only lived consequence can unify perception across propaganda divides.
Why “Crimes Against Children” Becomes a Unifying Trigger
Q Post #4908 includes the idea that crimes against children “unite all humanity.” Whether or not readers agree with every implication people attach to that phrase, the psychological point is sound:
There are issues that cut across:
party lines,
identity lines,
and propaganda segmentation.
In 5GW, such issues function as moral overrides, they break political trance states because they activate a deeper human layer than ideology: protection of the innocent.
Operationally, this matters because it creates a potential unity vector in a population that has been deliberately fragmented.
This is not about sensationalism. It’s about human behavior.
Game Theory: Why the Enemy Couldn’t Be Defeated Head-On
Q Post #4024 references game theory for a reason.
If an entrenched system controls:
communications,
institutions,
enforcement mechanisms,
and narrative legitimacy,
then a direct confrontation tends to fail. The adversary:
reframes the attacker as the threat,
uses institutional legitimacy as armor,
and isolates dissenters as extremists.
Game theory solutions in this context are indirect:
force contradictions,
induce overreach,
create dilemmas where every response harms credibility,
push the system into exposing itself.
Phase 5 is that strategy in action.
Movie I and Movie II create a dilemma for the entrenched system:
If they suppress and censor, they reveal fear and control.
If they allow discussion, they lose narrative monopoly.
If they prosecute opponents aggressively, they reveal selective justice.
If they do nothing, public confidence collapses anyway.
Either way, legitimacy bleeds out.
That is how deeply entrenched control systems fall…not from a single blow, but from forced self-exposure.
Phase 5 End State
Phase 5 is complete when a critical mass of the public reaches the same conclusion independently:
The system is not neutral.
Institutions coordinate to preserve continuity.
Narratives are deployed to manage perception of outcomes.
The population is the target, morale is the terrain.
At that point, something changes that no censorship can reverse:
People stop asking permission to recognize reality.
And once that happens, the next phase becomes possible.
Key Takeaway
Phase 5 is where the operation moves from information to will.
Because you can’t “tell” a nation out of a trance.
You must “show” it…long enough, clearly enough, painfully enough, that the spell breaks on its own.
That is the doctrine behind the movies.
Skeptic Sidebar: Good-Faith Skeptic vs. Weaponized Skeptic
Let me speak directly to the skeptic, because you’re necessary in an information war. Healthy skepticism is how you prevent groupthink, grift, and self-deception.
But understand this: in Fifth Generation Warfare, “skepticism” can also be weaponized.
A hostile operator doesn’t have to prove you wrong. They only have to keep you stuck, permanently questioning, permanently delaying, permanently “waiting for more proof,” until momentum dies and morale collapses.
So here’s the difference.
Good-Faith Skepticism (Valuable)
A real skeptic tends to:
Ask clear, specific questions (“What evidence would falsify this?” “What’s the mechanism?” “What’s the timeline?”)
Apply the same standard to all sides (not just the side they dislike)
Seek primary sources and pattern-level reasoning
Accept “I don’t know yet” as a legitimate temporary position
Update conclusions when new facts appear
Good-faith skepticism sharpens the blade.
Weaponized Skepticism (Disruptive)
A bad actor - whether an ideological partisan, a grifter, or an influence operator - often:
Demands an impossible standard (“Prove the entire theory beyond any doubt or it’s all false.”)
Uses endless deflection (“Could be coincidence” → forever, regardless of accumulation)
Moves goalposts (“That’s not enough” → but never defines what would be enough)
Attacks motive instead of addressing structure (“You just want to believe”)
Floods with cynicism to induce fatigue (“Nothing matters. Everyone’s controlled. It’s pointless.”)
That isn’t skepticism. That’s paralysis-by-doubt.
The Rule for This Series
This article is not asking you to “believe.”
It’s offering an operational model.
So judge it like you’d judge any serious model:
Does it explain sequencing?
Does it predict incentives and institutional behavior?
Does it account for countermeasures and narrative control?
Does it remain internally consistent across phases?
If you disagree, don’t just say “prove it.”
Say where the model breaks and what alternative mechanism explains the same outcomes better.
Why I’m Flagging This Now
As this series escalates into later phases, especially the exposure and cleanup phases - expect a predictable response: people will appear who sound like skeptics but function like fog machines, turning every point into a circular stall.
Consider this your early warning.
And to be clear: the anatomy of controlled opposition, false MAGA, and psy-ops actors, including how “professional skeptics” are used to exhaust movements, will be addressed comprehensively in Phase 9. That phase is where we name the tactics, map the behavior, and show you how to spot it in real time.
For now, here’s the only filter you need:
A real skeptic seeks clarity. A weaponized skeptic seeks delay.
If you’re the real one, good. Stay with me.
Because Phase 9 is going to make a lot of “skeptics” very uncomfortable.
Next:
Phase 6 – The Responsibility Shift
“We The People” as the Center of Gravity
Phase 6: The Responsibility Shift
“We The People” as the Center of Gravity
If Phase 5 was the demonstration, Phase 6 is the conversion.
This is the phase where the operation stops treating the public as an audience and begins treating the public as the decisive terrain, the center of gravity in the conflict.
Because in Fifth Generation Warfare, you can expose a system a thousand times…
…but if the population remains psychologically conditioned to outsource responsibility, the system survives.
Phase 6 exists to answer the most operational question of the entire doctrine:
Who actually has to act for the plan to succeed?
And the answer…by design…is not “Q,” not “Trump,” not “a savior,” not “the courts,” not just “the military.”
It’s the citizenry.
The Center of Gravity Principle
In military planning, every campaign identifies a center of gravity - the thing that, if influenced or controlled, determines victory.
In a kinetic war, it might be:
An enemy capital
A logistics pipeline
Command and control
In 5GW, the center of gravity is almost always:
Public perception
Public cohesion
Public will
And specifically: public willingness to act without permission.
Phase 6 is where the public is moved from:
spectator mode → stakeholder mode
outrage mode → agency mode
dependency → ownership
Why This Shift Had to Be Forced, Not Suggested
Human behavior is predictable under stress.
In high-crime policing and long investigations, you learn quickly: most people want the truth… as long as it costs them nothing.
They want:
someone else to confront danger
someone else to make the report
someone else to testify
someone else to take the blowback
And in national terms, the same pattern emerges:
People want the country saved, but they want it saved by:
“the next election”
“the courts”
“the right agency”
“someone in charge”
That reflex, outsourcing sovereignty, is the psychological vulnerability the operation had to break.
You cannot have a sovereign nation with a dependent population.
So Phase 6 is where the plan stops feeding comfort and begins building capacity.
The Moral Injury Problem
Phase 6 also addresses something deeper: moral injury.
In war, moral injury happens when people realize:
institutions failed them
leadership betrayed them
rules were selectively applied
truth was weaponized
The result is often:
bitterness
paralysis
“what’s the point?”
retreat into distractions
The Deep State (or any entrenched control system) doesn’t need everyone to agree with it.
It only needs the public to become:
exhausted
divided
cynical
inactive
Phase 6 is designed to prevent that outcome.
It reframes the psychological injury into a mission:
“This is not the end of your belief in America.
This is the beginning of your responsibility for it.”
That single reframing converts despair into direction.
And in 5GW, direction is morale.
The Sovereignty Transfer: From Leaders to Citizens
A key concept in clandestine operations and population-control models is this:
If people believe only authorities can act, then authorities can be captured and controlled.
If people believe they themselves must act, capture becomes exponentially harder.
Phase 6 reinforces a principle so old it’s almost invisible:
Sovereignty is not a concept. It’s a behavior.
It shows the public that the operational solution is not:
waiting for permission
waiting for perfection
waiting for “the big reveal”
It is:
building local strength
building civic courage
building social cohesion
building institutional pressure from the bottom up
In law enforcement terms, it’s the moment a community stops saying “someone should do something” and starts saying “we’re done tolerating this.”
Why “We The People” Is Not a Slogan
If “We The People” is just a motivational phrase, it’s useless.
In Phase 6, it becomes an operational directive:
Information discipline (don’t become a rumor carrier)
Community building (isolation is how psy-ops win)
Local pressure (local levers move faster than federal fantasy)
Election participation (scale matters, so does staffing and oversight)
Noncompliance with psychological manipulation (fear-based narratives, rage bait, despair loops)
This is how populations become uncontrollable.
Not by being louder.
By being steadier.
MORALE AS A WEAPON
This phase also sharpens a concept most people misunderstand:
Morale is not optimism. Morale is stability under pressure.
Optimism can be faked.
Stability cannot.
A population with disciplined morale:
doesn’t panic at headlines
doesn’t fracture under pressure events
doesn’t turn on itself when provoked
doesn’t collapse into apathy when timelines slip
That’s why the information war constantly tries to produce:
fear surges
outrage surges
despair surges
Those are not emotions.
They are operational effects.
Phase 6 teaches readers to treat emotion like an indicator light on a dashboard:
If it’s flaring, someone is likely pulling a lever.
Phase 6 End State
Phase 6 is complete when a critical mass of citizens internalize three truths:
No institution will save what the people won’t defend.
Sovereignty requires participation, not spectatorship.
The population’s will is the battlefield and morale is the decisive weapon.
At that point, the operation has achieved something bigger than exposure:
It has created a public that cannot be psychologically managed the way it was before.
Key Takeaway
Phase 5 showed people what the system can do.
Phase 6 forces the only conclusion that matters:
If you want the country back, you must act like it belongs to you.
Not in violence.
Not in chaos.
In discipline, participation, community, and unbreakable civic will.
That is what “We The People” means when it stops being a quote and becomes a posture.
Next:
Phase 7 – Electoral Overwhelm
How overwhelming turnout, visibility, and citizen-level engagement are used to break manipulation, without relying on institutions to police themselves.
Phase 7: Electoral Overwhelm
The Strategic Win - Breaking the Fraud Machine by Scale and Restoring Morale
Phase 7 is not just about winning an election.
In this operational framework, Phase 7 is about achieving something far more important in Fifth Generation Warfare:
a decisive, measurable, morale-restoring victory that the public can feel.
After six phases of psychological strain - exposure, uncertainty, institutional distrust, narrative warfare, social division, and lived pressure, an operation must deliver a win the population can recognize. Without that, you risk a predictable breakdown:
fatigue becomes apathy
apathy becomes disengagement
disengagement becomes defeat - without a shot fired
This is a core 5GW reality: morale is not a side effect. Morale is a strategic asset.
That is why Phase 7 is placed where it is. It is not an accident of timing.
It is a necessary morale injection, designed to convert awareness into renewed will.
Why a “Win” Becomes Operationally Necessary
In kinetic war, battles are fought for terrain.
In 5GW, battles are fought for belief in the possibility of victory.
If the population believes:
“nothing matters”
“it’s all rigged”
“they always win”
…then the adversary doesn’t need to censor you. They don’t need to arrest you. They don’t need to stop you.
You stop yourself.
So Phase 7 functions like a controlled counteroffensive: it does two things at once.
Operational: it overwhelms manipulation capacity (in this model).
Psychological: it restores agency “We can win.”
You cannot sustain a long operation on exposure alone.
Exposure without victory produces despair.
Victory converts exposure into action.
The Concept of Electoral Overwhelm
Electoral overwhelm is simple in concept and brutal in effect:
Win by a margin large enough that manipulation cannot be executed quietly, cleanly, or plausibly.
This is not merely a political strategy. It is a systems strategy.
In this theory, the problem is not one mechanism. It is an ecosystem:
narrative shaping
institutional friction
procedural ambiguity
administrative choke points
legal delays
trust erosion
So the counter is not one tactic.
It’s mass participation and visibility - scale that breaks the machine.
Overwhelm doesn’t require perfection.
It requires pressure.
Why Phase 7 Comes After Phase 6
Phase 6 establishes the decisive truth of this entire doctrine:
“We the People” are the center of gravity.
Phase 7 is the first time that realization is converted into a single, unified, real-world demonstration.
Phases 1–6 are preparation and conditioning:
the population learns the battlefield (media)
learns investigative posture (participation)
learns psychological warfare (discipline)
recognizes continuity planning (structure)
internalizes consequence (lived proof)
accepts responsibility (agency)
Phase 7 is where agency becomes measurable.
This is the shift from:
“I see it”
to“I moved it.”
That’s why it matters.
The Morale Component: The Win as a Weapon
This phase is also deliberately positioned because the population needs a psychological reversal.
After years of:
gaslighting
censorship
ridicule
institutional demoralization
“you’re powerless” messaging
…a win does something profound.
It changes what people believe is possible.
In 5GW, that’s a weapon.
A victory:
breaks learned helplessness
collapses fear of speaking
restores recruitment energy
reactivates disengaged citizens
destabilizes the adversary’s psychological advantage
The opposition can survive criticism.
It struggles to survive confidence.
How Overwhelm Functions as a Counter-Op
From an operational planning lens, overwhelm creates multiple simultaneous effects:
1) Reduces the effectiveness of narrative control
When participation is visible and widespread, manufactured consensus becomes harder to maintain.
2) Increases the cost of interference
The more eyes on the process, the more friction any manipulation creates, and the harder it is to contain downstream consequences (legal, reputational, institutional).
3) Forces exposure through scale
Large margins and high participation reduce ambiguity and increase scrutiny.
4) Recruits new participants through momentum
Victory is contagious. It pulls in fence-sitters who avoid “losing teams.”
Skeptic Reality Check
If you’re a genuine skeptic reading this: treat “electoral overwhelm” here as a strategic theory, a model of how large-scale participation can reduce the impact of contested mechanisms and amplify transparency pressure.
You don’t have to accept every premise to recognize the logic:
systems protected by ambiguity struggle under visibility
morale collapses are exploited; morale surges disrupt
scale changes the cost structure of interference
The underlying point stands even if your interpretation of recent history differs.
Phase 7 End State
Phase 7 is complete when three things happen:
The population experiences proof of agency
They feel: “My participation mattered.”The adversary’s dominance narrative fractures
“You can’t win” becomes less believable.The operation gains momentum to move into dismantlement
Because now you have what every serious campaign requires:
public will + public energy + public confidence.
And that is what Phase 8 needs.
Key Takeaway
Phase 7 is not simply a win.
It is a morale operation embedded inside an electoral event.
A psychological counterstrike.
Because in 5GW, the side that controls morale controls time.
And the side that controls time controls outcomes.
Next:
Phase 8 - Destroying the Deep State Infrastructure
Cutting financial arteries, exposing laundering pathways, and dismantling institutional scaffolding.
Phase 8: Financial Exposure
Cutting the Funding Arteries - USAID, NED, NGOs, and the Money Pathways That Power Influence
Phase 8 is where the operation shifts from belief-space to ledger-space.
In military planning, you don’t defeat an enemy force by arguing with it. You defeat it by collapsing its:
logistics
resupply
communications
protection networks
In law enforcement - especially gangs, corruption cases, organized crime - this is the same doctrine with a different name:
Follow the money.
Because money is more honest than people.
Money reveals structure.
And structure reveals intent.
Phase 8 is built on a simple operational truth:
Narratives are expensive.
Influence operations don’t run on ideology alone. They run on funding pipelines, grant networks, contract vehicles, and institutionalized cash flow that can be disguised as “development,” “training,” “capacity building,” “consulting,” “research,” or “subscriptions.”
This phase is about exposing the infrastructure, not just the personalities.
The DOGE-Style Transparency Shock
A key accelerant in this phase - per reporting at the time - was the emergence of Elon Musk’s “Department of Government Efficiency” (DOGE) as a cost-cutting/transparency initiative inside the federal government. (TIME)
Whether you view DOGE as a political instrument, a reform project, or both, the operational utility is straightforward:
It forces visibility
It normalizes auditing
It turns procurement data into a public battlefield
And once spending becomes a public battlespace, the old model…quiet funding, low scrutiny, narrative cover - starts to fail.
What This Phase Is and What It Is Not
Phase 8 is not “every dollar equals corruption.”
Phase 8 is: identifying the pathways that can be exploited and exposing how money can serve narrative control, directly or indirectly.
In investigations, you don’t start by declaring guilt.
You start by mapping:
Who funds what
Through which intermediaries
With what oversight
With what dependencies created
That’s Phase 8.
Exhibit A: USAID Media Support
This is a widely reported set of figures:
training/support for 6,200 journalists
support for 707 non-state/independent media outlets
support for 279 media-sector civil society organizations (CSOs)
These figures were reported as coming from a USAID fact sheet (later removed) and surfaced in coverage and press-freedom reporting. (Reporters Sans Frontières)
Important distinction:
This has been framed publicly as journalism development / independent media support - not “paying influencers for propaganda.” (FactCheck.org)
So why does it matter in Phase 8?
Because in information warfare, funding dependence creates leverage even without explicit editorial control.
This doesn’t require a cartoonish “payoff.”
It can operate through:
selection (who gets funded and who doesn’t)
dependency (who can survive without funding)
incentives (what kinds of “approved” narratives keep grants flowing)
In law enforcement terms: you don’t need to tell the crew what to do every day if you control the paycheck and the permissions.
This is about structure, not slogans.
Exhibit B: Government “Subscriptions” to Media Services
Here is a second set of reports: federal agencies paying for subscriptions to services like Politico Pro, Reuters, and major newspapers as part of research/informational needs.
Multiple outlets and fact checks emphasized these were procurement/subscription transactions, not “grants” or “payoffs for coverage.” (FactCheck.org)
This matters for Phase 8 in a different way:
It proves a baseline reality: the government buys access to information tools.
It creates an optics battlefield: activists and operatives can misframe procurement as “payments for propaganda.” (FactCheck.org)
It highlights how easily narratives can be weaponized in both directions:
one side screams “payoffs”
the other side says “nothing to see here”
and the public never learns the real lesson: money pathways = influence potential.
This is exactly how information war stays foggy, “Fog of War” in the digital battlefield.
The Real Target of Phase 8
Phase 8 isn’t about one agency or one contract line.
It’s about the ecosystem:
primary funding sources
intermediary NGOs and contractors
subgrants
“capacity-building” programs
compliance structures that shield accountability
media/think tank/advocacy networks that shape perception
In operational planning terms, this is enemy infrastructure.
And once infrastructure is mapped, three things become possible:
defunding
prosecution (where criminality is present)
public inoculation against narrative manipulation
How to Audit This Like an Investigator
This is where my law enforcement experience becomes a weapon for you.
In financial cases, you build a map:
Source (appropriation / budget line / agency)
Vehicle (grant, contract, cooperative agreement, subaward)
Cutout (NGO, partner org, subcontractor)
Destination (program, media outlet, training org, “initiative”)
Outcome (influence, dependency, narrative alignment, operational effect)
This is the discipline Phase 8 installs:
stop arguing personalities
start tracing systems
stop reacting to headlines
start pulling receipts
That’s how you win a long war.
Phase 8 End State
Phase 8 is complete when:
the public understands how influence is funded
spending pipelines are visible enough to be contested
institutions can’t hide behind labels like “aid,” “development,” or “subscriptions” to avoid scrutiny
the population learns to separate:
legitimate program intent from
structural vulnerability to narrative capture
Key Takeaway
Phase 8 isn’t “trust me bro.”
It’s show me the ledger.
Because once the funding architecture becomes visible, the operation graduates from conversation to consequence.
And this is exactly where the next fight begins.
Because when you expose money pathways, you trigger a predictable counter-move:
Controlled opposition floods the zone.
Some will pretend to be your ally while steering your conclusions.
Some will pretend to be skeptical while poisoning inquiry.
Some will weaponize half-truths (“payoffs!”) to discredit the entire audit effort, while others will use dismissive half-truths (“just subscriptions!”) to keep the public from learning anything structural.
That is Phase 9.
We’re going to name the tactics, the actors, the camouflage, and the psychology - so real skeptics aren’t manipulated and real patriots aren’t baited.
Phase 9: Controlled Opposition Cleanup - RINOs, False MAGA, PreTenders and Psy-Ops Actors
The Counter-Infiltration Phase (and why it always arrives right after the money trail is exposed)
If Phase 8 is the financial X-ray, the audit lens that reveals where the bloodstream of power actually flows, then Phase 9 is the inevitable next move: the organism reacts.
When funding pathways, influence pipelines, and institutional “information shaping” mechanisms get exposed, you don’t just see bureaucrats scramble. You see voices scramble.
Some pivot quietly. Some attack loudly. Some ignite feuds. Some suddenly “discover principles” they never applied consistently…right on cue.
That is not a conspiracy theory. That is standard counter-infiltration reality in every battlespace I’ve ever operated in - military, law enforcement, or intelligence-adjacent: when a network is threatened, it deploys buffers, cutouts, and chaos to protect the core.
The Phase 9 mission (simple, brutal, necessary)
Phase 9 exists to protect the movement from a predictable tactic:
In 5GW, you don’t have to defeat a population. You only have to fracture it.
So the enemy doesn’t only run propaganda through mainstream media. It also runs fracture operations through “friendly” channels, people who already have your trust, your attention, your emotional buy-in.
And right now, in my assessment, we’re watching this phase unfold in real time.
The Two Infiltration Models You Must Understand
Model A: The “Sincere Turncoat”
A voice supports MAGA/Trump, gains trust, then breaks: sometimes out of ego, money, ideology, or opportunism.
That’s common. It’s human.
Model B: The “Constructed Rapport Asset”
A voice builds a conservative/MAGA identity specifically to bank trust, then flips on cue to accomplish a timed objective:
fracture the base
demoralize the operators
redirect anger away from the real enemy
ignite internal purges
turn “We the People” into tribal warfare
In counterintelligence terms, you’re not looking for “bad opinions.”
You’re looking for operational effect.
Phase 9 is about effect.
The “Money Trail” Trigger (Why Phase 9 follows Phase 8)
Once you shine light on how narrative ecosystems get shaped - via training programs, NGO networks, procurement contracts, and influence-adjacent funding streams - you force a reaction.
Two recent examples help establish the terrain:
USAID did fund training/support for thousands of journalists and supported hundreds of outlets globally (often described as “media development” / “strengthening independent media”). (Reporters Without Borders)
U.S. agencies have also paid for subscriptions to paywalled services (Politico Pro, Reuters, NYT, etc.) as a procurement/research practice, often misrepresented online as “payoffs,” but commonly documented as subscription contracts. (FactCheck.org)
Now…notice the key here:
You don’t need to claim every program is “propaganda payments” to understand the operational reality: money builds access; access builds influence; influence shapes perception.
Phase 9 is what happens when the audience starts seeing that machinery.
The Tell-Tale Pattern: “Trump Betrayed MAGA” as a Coordinated Emotional Wedge
Here is the pattern I want my smart skeptics to track like a detective:
Build trust inside the tribe
Wait until exposure pressure rises (audits, releases, investigations, money trail attention)
Flip to a singular emotional frame:
“Trump betrayed you.”Demand the audience redirect anger inward
Ignite public feuds so the base spends its energy fighting itself
Whether those actors are compromised, captured, ego-driven, or simply incentivized, the effect is the same: fracture.
And the effect is the mission.
Real Skeptics vs. Counterfeit “Skeptics” (Read This Carefully)
I respect real skepticism. Real skepticism strengthens operations.
But there is also a weaponized impersonation of skepticism that appears in every influence war:
The Real Skeptic
asks for sourcing
distinguishes fact vs inference
tests claims consistently (including against “their side”)
stays on mission: truth, clarity, outcomes
The Counterfeit Skeptic (Phase 9 actor)
argues process endlessly to stall conclusions (“nothing can be known”)
demands perfection only from your side
mocks morale, unity, and resolve as “cultish”
reframes every exposure as “distraction”
never proposes a better model…only paralysis
In homicide work, we had a phrase: “Confusion is a suspect’s best friend.”
So here’s the rule of engagement:
If a “skeptic” consistently produces demoralization and fragmentation as the end product, treat them as a hostile influence node until proven otherwise.
And yes, this exact counterfeit-skeptic tactic will be addressed in full under Phase 9’s broader “controlled opposition” framework, because it is one of the most effective sabotage tools in modern information warfare.
Case Study: The Elected-Official Flip Nodes (MTG, Massie)
I’m going to name names here because Phase 9 is where names matter.
Marjorie Taylor Greene (MTG): The whiplash problem
Regardless of how anyone feels about her personally, the operational issue is the speed and public theater of the break, because high-visibility breaks become rally points for fracture.
Trump’s own public language about Greene became blunt. In one Truth Social post reported by CBS, Trump wrote she is “not AMERICA FIRST or MAGA” and attacked her credibility in harsh terms. (CBS News)
PBS also reported Trump withdrawing support/endorsement and accusing her of going “Far Left,” characterizing her recent posture as constant “complain.” (PBS)
Operational takeaway: when a high-profile figure with a MAGA brand becomes a constant public amplifier of internal resentment, the movement must treat it as a fracture vector, not a “leader.”
Thomas Massie: The pressure-point exploitation problem
Massie is a different case: not a personality-driven public break, but a recurring pattern of positioning where the headline outcome is internal division and redirected anger.
Trump has repeatedly attacked Massie in strong terms over years - calling him a “third rate Grandstander” in 2020. (X (formerly Twitter))
In 2025 coverage, Trump labeled Massie a “LOSER,” and described him as “weak,” “ineffective,” and someone who “votes ‘NO’ on virtually everything.” (Fox News)
Operational takeaway: you don’t have to agree with Trump’s tone to see the larger point, internal saboteurs don’t need to be Democrats. They only need to be consistent friction sources at strategic moments.
The Influencer Civil War: A Digital Battlefield Classic
Now zoom out: Phase 9 isn’t only elected officials. It’s attention warfare.
We are watching public infighting among major right-wing media/influencer nodes, an escalating “civil war” dynamic that multiple outlets have covered recently. (Forbes)
And yes, the names referenced are part of that visible arena:
Alex Jones
Candace Owens
Nick Fuentes
Tucker Carlson
plus a constellation of secondary influencers amplifying the feud cycle
You do not need to prove a single “handler” to understand the operational effect:
A deeply entrenched adversary doesn’t have to silence you, only keep you permanently fighting each other.
The public spectacle becomes the product. The base becomes emotionally exhausted. The real enemy becomes background noise.
That is the play.
The MSM “Face of MAGA” Trick (Rebranding by Containment)
Another Phase 9 tactic: legacy media attempts to assign leadership to the movement by naming “faces of MAGA,” often selecting figures most useful for containment, because if they can define your leaders, they can define your narrative boundaries.
Simultaneously, as mainstream credibility collapses, you’ll see institutional voices attempt to migrate into “alt media / citizen journalist” spaces and rebrand as if they were always independent.
Your job as a trained operator is not to panic at this.
Your job is to identify the entry points and watch for the patterns:
coordinated talking points
synchronized outrage timing
manufactured tribal binaries
and the constant attempt to redirect anger away from the administrative state and toward fellow citizens
Rules of Engagement for Digital Soldiers (Phase 9 Discipline)
Here is how you fight this phase without becoming what the enemy wants:
Do not feed tribal theater.
If a “war” produces clicks but no strategic gain, it’s a trap.Force specificity.
“Trump betrayed MAGA” is a slogan. Ask: What exact action? What evidence? What alternative plan? Who benefits from the fracture?Separate exposure from demoralization.
Exposure is necessary. Hopelessness is weaponized.Track timing like an investigator.
Watch flips, outrage cycles, and feuds relative to: audits, releases, deadlines, hearings, and money-trail scrutiny.Keep the enemy definition stable.
The core adversary is the entrenched institutional machinery that survives elections and governs through narrative control, not your neighbor with imperfect language.
Kayfabe: The New “Wait for the White Knight” Error
There’s a concept that keeps resurfacing inside movements under psychological pressure: kayfabe, the idea that public conflict is staged, scripted, or strategically “performed” to generate an effect.
Let’s be clear and disciplined:
Yes, real operations use misdirection.
Yes, information warfare includes theater.
Yes, “white hats” (or any competent counter-force) may deploy controlled narratives, decoys, and public-facing friction as part of a broader sequencing strategy.
But here is the trap:
When people label every public confrontation as kayfabe, they recreate the same passivity that Phase 1–3 was designed to destroy.
It becomes the updated version of the old error:
“Just wait. Don’t think. Don’t verify. It’s all part of the plan.”
That mindset is not strategic. It’s sedation.
In law enforcement terms, it’s the equivalent of watching suspects move money and saying, “It’s probably nothing,” because you want it to be nothing. That’s not investigation. That’s self-protection.
Even if something is kayfabe, it must still have an operational purpose:
What is the intended effect?
Who benefits from the timing?
What behavior is being driven?
What attention is being redirected?
Who gains cover while the crowd is distracted?
Kayfabe is never an excuse to stop thinking.
It is a reason to think harder.
The discipline is simple:
Investigate first.
Form hypotheses, not certainties.
Control reaction.
Measure outcomes.
Do not outsource judgment to personalities.
Because the Deep State doesn’t need to “defeat” you if it can train you to excuse everything and react to nothing.
That’s not resilience. That’s surrender dressed up as patience.
Point to Remember: The Influencer Wars Are Designed to Simulate a Civil War Inside MAGA
This is one of the oldest psychological warfare tricks in existence:
If you can’t defeat a movement head-on, you fracture it from the inside by making it feel like it’s tearing itself apart.
The influencer wars are designed to create the perception of:
Total internal collapse
Civil war inside the base
“No one can be trusted” paralysis
Demoralization through endless tribal conflict
The objective is not debate.
The objective is exhaustion.
In 5GW, you don’t have to make people lose a battle.
You just have to make them believe the war is hopeless.
So treat this for what it is: a morale attack.
Here’s the operating rule:
When the conversation becomes pure personality, the mission is being hijacked.
That doesn’t mean ignore public disputes. It means refuse to be captured by them.
Do not let a manufactured influencer civil war become your reality.
The real war is not “my personality vs your personality.”
The real war is the population vs the system that needs the population confused, divided, and demoralized.
And the most dangerous outcome isn’t choosing the wrong side of an influencer feud.
It’s letting the feud convince you that the entire mission is collapsing.
Hold the line. Keep the frame. Stay disciplined.
Because this phase ends the moment you stop being emotionally steerable.
Phase 9 End State
Phase 9 is complete when:
controlled-op fracture attempts fail to move the base
the audience stops taking bait from “influencer war” cycles
unity becomes discipline, not a mood
and the movement keeps its eyes on the actual targets: corruption networks, institutional capture, and accountability mechanisms coming next
Key Takeaway
Phase 9 is not “drama season.”
Phase 9 is the counter-infiltration season, the moment you learn who was real, who was rented, and who collapses when the mission requires discipline over attention.
And if you want the blunt truth?
The deeper the corruption exposure gets, the louder the controlled-op actors will scream, because noise is the last shield they have.
Next: Phase 10 - RICO Logic, Indictment Pathways, and Why “Case-Building” Takes Time
Phase 10: RICO, Indictments, and the Accountability Phase
Why “Nothing Is Happening” Is the Enemy’s Favorite Lie
Disclaimer (read this the right way): This phase is written as an operational analysis and training brief, not legal advice, and not a claim of guilt against any individual. It references public reporting and official releases where available, and it explains how complex enterprise cases are built in the real world.
Phase 10 is where the entire operation changes texture.
Up through Phase 9, you were watching the battlespace: narrative warfare, controlled opposition, morale attacks, and information traps designed to fracture the movement.
Phase 10 is where the war moves into legal gravity, where facts become filings, where patterns become predicates, and where “exposure” becomes accountability.
And the Deep State’s most reliable counter-attack begins right here:
“Nothing is happening.”
“No one will ever be held accountable.”
“Statute of limitations means it’s over.”
That line is not skepticism.
That line is demoralization doctrine.
Why the Accountability Phase Looks Slow (By Design)
Anyone who has worked long investigations - major cases, conspiracies, organized crime, corruption, task-force operations - knows this:
The public wants arrests. Investigators want enterprises.
In major enterprise cases, you do not charge the top first. You build:
the structure
the money pathways
the communication nodes
the decision authority
the concealment layer
the predicate acts that attach to the enterprise
You don’t swing at a headline.
You swing at the system.
That is why Phase 10 is often misread by emotionally hungry observers. They want dramatic moments. Real cases are built through boring mechanics: paper, timelines, witnesses, wire paths, predicate stacking, jurisdictional strategy, and controlled sequencing.
What a “Criminal Enterprise” Actually Means
A criminal enterprise, in RICO terms, is not “a gang in the street” only. It can be:
a formal organization
an informal association-in-fact
a network of actors working toward a shared goal
The legal center of gravity is not just “bad acts.” It’s coordinated conduct tied together by:
relationships
continuity
common purpose
a pattern of racketeering activity
That’s why enterprise cases terrify entrenched power. They turn “isolated scandal” into organized system.
The statute (18 U.S.C. § 1961) defines what qualifies as “racketeering activity,” and it’s broad for a reason. (Legal Information Institute)
And the U.S. Sentencing Commission’s RICO primer explains the purpose bluntly: RICO is built to address ongoing criminal organizations and the infiltration of legitimate structures. (United States Sentencing Commission)
The Continuing Conspiracy Doctrine: Why “Statute of Limitations” Isn’t a Magic Shield
Here is the operational answer to the demoralization line.
Conspiracy is a continuing offense.
For many conspiracy statutes that require an overt act (like 18 U.S.C. § 371), the statute of limitations generally runs from the last overt act in furtherance of the conspiracy, not the first one. (Department of Justice)
This matters because it neutralizes one of the most common influence ops used against your morale:
“Too much time has passed, nothing can happen.”
That claim is often either ignorant… or weaponized.
If the conduct continued, if concealment continued, if acts in furtherance continued then the legal clock argument is not as simple as keyboard lawyers pretend.
And strategically, the statute of limitations debate is also a tell: it’s one of the first talking points deployed when people sense a case is moving from “narrative” to “legal.”
Why RICO Changes the Battlefield
RICO is not just a charge, it’s a strategy.
It allows prosecutors to:
show pattern, not one-off events
show coordination, not coincidence
connect actors who never touched the same document
convert “unrelated controversies” into one enterprise story
In policing terms: it’s the difference between arresting individual dealers… and taking down the distribution network.
That’s why Phase 10 is a morale battle. Because the minute enterprise theory enters the public consciousness, the enemy must do everything possible to convince people it will never happen.
Signals That Phase 10 Is Live
1) Russia-hoax accountability is being treated as a formal investigative lane
DNI Tulsi Gabbard released declassified material related to what her office frames as a manufactured “Russia hoax,” and Reuters reported the Justice Department forming a “strike force” to assess claims of alleged weaponization connected to those disclosures. (Director of National Intelligence)
Whether one agrees with the framing or not, that is a key Phase 10 marker: movement from commentary into investigative architecture.
2) John Bolton indictment as a visible “enterprise-style” prosecution signal
A Maryland grand jury indictment of John Bolton has been widely reported, with detailed breakdowns available from PBS and analysis from legal outlets. (PBS)
You don’t need to overstate it. The point for Phase 10 is simple: high-level cases are being pursued and litigated in the open, which has downstream effects on witness decisions and institutional risk calculations.
3) James Comey case illustrates both action and friction
Reporting shows Comey was indicted, and later a judge dismissed the case based on a finding that the prosecutor was unlawfully appointed, while noting it could potentially be refiled, though the statute-of-limitations issues complicate that path. (AP News)
For Phase 10, this is important for training: accountability phases are contested. Procedure becomes battlefield. The defense doesn’t only argue facts; it attacks process, authority, venue, and appointment legitimacy.
That’s not failure…that’s what real legal war looks like.
4) John Brennan: “subject of an investigation” is not the same as “indicted” but it’s still a marker
Public reporting indicates Brennan’s attorneys sought court intervention related to an investigation and concerns about venue/judge assignment. That supports the narrower, defensible statement: there is a known investigative lane touching Brennan, contested through legal maneuvers. (Bloomberg Law)
So we keep it precise:
Investigation signals are real signals
Indictment claims require confirmation
Phase 10 is about architecture, not hype
Counter-Demoralization: The “Nothing Will Happen” Script
If someone, especially a self-branded “skeptic” shows up to say:
“No one is ever held accountable.”
“Statute of limitations means it’s dead.”
“This is all performative.”
…you now have a disciplined response:
Enterprise cases are built, not announced.
Conspiracy is continuing, limitations arguments are not one-size-fits-all. (Department of Justice)
The presence of contested procedures is evidence of stakes, not proof of nothing. (AP News)
The enemy’s best move is to convince you to emotionally quit before legal gravity hits.
Phase 10 is where they push hardest for despair, because despair is the only thing that can stop a population from sustaining pressure long enough for the system to turn.
Forward-Looking Note: Multiple RICO Lanes and the Epstein Prediction
Operational Forecast: When networks involve long-running coordination, concealment, facilitation, finance, and institutional shielding, enterprise frameworks become attractive tools. It would not be surprising to see additional enterprise-style prosecutions develop, potentially including renewed, structured Epstein-related efforts, because RICO is built for exactly that kind of continuity and coordination. Epstein RICO is coming….
Phase 10 End State
Phase 10 is complete when:
enterprise structures are identified publicly or in court
predicate acts are stacked into coherent patterns
cooperating witnesses begin to flip at scale
“untouchables” become legally reachable
At that point, Phase 11 becomes inevitable.
Because once the system is on legal defense, it can’t run elections the same way.
Key Takeaway
Phase 10 is where narrative war meets legal war.
The enemy can survive accusations.
It struggles under exposure.
It collapses under enterprise accountability.
And that is why the first thing it tries to kill… is your morale.
Operational Note: From Assessment to Game Theory (Phases 11-17)
The preceding phases establish an operational framework for understanding information warfare, institutional capture, and exposure sequencing. Beginning with Phase 11, the analysis shifts from retrospective assessment to forward-looking game theory. These phases are presented as doctrinal projections, plausible campaign pathways modeled through principles of strategic design, psychological operations, counter-network disruption, and institutional leverage. The aim is not prediction for its own sake, but disciplined anticipation: identifying likely moves, likely counter-moves, and the conditions under which momentum is preserved, morale is protected, and strategic advantage is consolidated.
Phase 11: Election System Lock-In
Voter Identity, Paper Truth, Midterm Control, and the End of Procedural Theater
Phase 11 is the institutional consolidation phase, the point where exposure and legal warfare must translate into permanent control of election mechanics. In operational terms, this phase is not about “winning an election.” It is about securing the machinery of legitimacy so the system cannot absorb exposure, swap faces, and quietly restore the same capture under new branding.
This phase exists for one reason:
Without election-system lock-in, every prior phase remains reversible.
The adversary’s most reliable counter-move after exposure is always the same: reset public memory, reassert control through procedure, and weaponize confusion until fatigue replaces focus. Phase 11 is built to prevent the reset.
Strategic Objective
To restore a system where election outcomes are verifiable, auditable, and enforceable, not “trusted” by narrative pressure. The mission is not partisanship; the mission is process integrity that holds up under hostile audit, hostile courts, hostile media, and hostile foreign influence operations.
The Integrity Package: Identity, Timing, and Paper Reality
Captured systems thrive on ambiguity and unverifiability. Phase 11 hardens elections through three simple pillars that reduce attack surface and restore public confidence:
1) Voter ID as a Baseline Standard
Identity verification is routine in every serious institution: banking, travel, licensing, employment, evidence processing. Elections, where sovereignty is decided, cannot remain the only domain where identity verification is treated as suspicious.
2) Same-Day Voting as the Default
Extended ballot windows increase chain-of-custody complexity, expand administrative discretion, and multiply opportunities for litigation warfare. Same-day voting compresses the operational window, strengthens oversight, and reduces the “gray zone” where manipulation thrives. Exceptions may exist for military and narrowly defined hardship cases, but the standard becomes simple: election day is election day.
3) Paper Ballots as the Source of Truth
Phase 11 requires a return to paper-based reality because paper creates a physical, auditable record that is resilient against digital tampering narratives and foreign influence claims. The center of gravity becomes:
hand-marked paper ballots
transparent custody
observable counting
auditable reconciliation
Machines, if used at all, become secondary tools, never the authority. The ballot itself becomes the authority.
Midterms as the Operational Fulcrum
Midterms are the hinge event that determines whether exposure becomes a flare or becomes a permanent shift. Control of election mechanics determines control of:
oversight committees and subpoena power
budget authority and institutional reform
the protection or sabotage of investigations
the survivability of legal warfare already underway
Phase 11 is successful when midterms function as a validation event: proof that reforms have altered the operational environment and cannot be undone by narrative pressure.
The 2020 Legitimacy Collapse: Why Lock-In Is Non-Negotiable
Phase 11 is inseparable from the legitimacy wound created by 2020 and other contested elections. Regardless of which narrative a person accepts, one reality is undeniable:
A system that cannot be transparently verified will remain permanently destabilized.
When public trust fractures, adversaries exploit the divide. They do not need to “win” the argument; they only need to ensure the population never regains a shared basis for legitimacy.
That is why Phase 11 does not treat election integrity as optional. It is sovereignty infrastructure. It is national security.
Fulton County as a Case Study in Process Failure and Trust Collapse
Election integrity is an evidence problem. Evidence requires documentation. Documentation requires custody and signature discipline.
In late 2025 reporting, Fulton County officials acknowledged documentation failures involving tabulator tapes and related records connected to the 2020 election - raising process-integrity concerns that intensify distrust even when fraud claims are contested. Federal litigation also emerged seeking access to Fulton County ballot materials and records.
Fulton County admits to verifying 315,000 votes in 2020 without poll worker signatures
The Phase 11 lesson is structural: even the appearance of broken procedure destroys legitimacy and broken procedure creates the exact environment where conspiracies, foreign influence narratives, and internal demoralization campaigns thrive.
A sovereign election system cannot rely on “assurances.” It must rely on auditable proof.
Foreign Influence and Voting-System Risk: Why the Digital Attack Surface Must Shrink
In an era of cyber operations, influence warfare, and transnational intelligence conflict, elections are a priority target - whether the attack is real, attempted, or merely perceived. Perception alone can destabilize a nation if the system is not verifiable.
This is why Phase 11 reduces digital attack surface and removes ambiguity:
paper as the record
transparent custody
observable counting
consistent standards
rapid, meaningful audits
A system that is verifiable does not fear allegations. It neutralizes them.
The Byrne/Maduro Vector as Game Theory: Why Disclosures Could Become Catalysts
Phase 11 also accounts for an operational reality: high-profile events and claims can function as accelerants for reform, whether or not every claim is ultimately proven.
Public statements by Patrick Byrne involving intelligence-adjacent assertions and election-system narratives have circulated widely for years and remain heavily disputed in public discourse. Separately, the U.S. capture of Nicolás Maduro introduces a new possibility space: cooperation, compelled disclosures, or intelligence exploitation could produce revelations - real or alleged - about transnational networks, financial channels, or influence operations tied to elections.
This is not presented as certainty. It is presented as game theory: if election legitimacy is a strategic center of gravity, then high-level disclosures - true, false, partial, or weaponized - will be used to force systemic change. That is exactly why lock-in must be implemented as policy and process, not as reaction to headlines.
Venezuelan government defector confirms that no elections run on Smartmatic or Dominion are secure.
Accountability Is a MUST/SHALL, Not a “Should”
Phase 11 requires a hard standard:
If criminal conduct exists, it must be investigated. If evidence supports charges, accountability must follow.
A sovereign nation cannot normalize the belief that election manipulation is consequence-free. That belief becomes an invitation for escalation, domestic and foreign.
This phase therefore includes:
audits that are real, not performative
investigations that follow evidence, not politics
prosecution standards built for court survivability
and reforms that remove ambiguity so future allegations are either proven or disproven quickly
The purpose is not perpetual controversy. The purpose is to end it, by making elections boringly verifiable.
Phase 11 End State
Phase 11 is complete when:
voter identity standards are normalized
same-day voting is restored as the default operating model
paper ballots become the authoritative record
custody and documentation standards become enforceable
audits are fast, meaningful, and repeatable
process violations carry real consequences
and election legitimacy becomes resilient against influence operations and morale attacks
At that point, the adversary loses a primary continuity tool: the ability to manipulate outcomes, or destabilize outcomes, through opaque procedure and narrative warfare.
If Phase 11 fails, everything collapses back into the same cycle - exposure becomes a headline, accountability becomes a moment, and the system resets itself through procedure. Without election-system lock-in, nothing else matters. This phase is not optional. It is the hinge point: it must succeed completely, or the entire operation fails.
Key Takeaway
Phase 10 builds legal consequence.
Phase 11 prevents procedural reset.
Exposure without lock-in becomes history.
Lock-in converts exposure into permanence.
Next: Phase 12 - Sovereign Alliance Reveal
Redefining “enemies,” exposing supranational control structures, and revealing the next layer of the battlespace.
Phase 12: The Sovereign Alliance - What It Is, Why It’s Forming, and What It Changes
Phase 12 is the geopolitical pivot in the doctrine: the moment the conflict stops presenting as “domestic politics” and starts presenting as what it has always been in Fifth Generation Warfare…a sovereignty war.
In this model, the world is not divided into friends and enemies. It is divided into:
Sovereign interests (nations attempting to reclaim independent decision-making), and
Supranational capture systems (networks that profit from dependency, endless war, debt leverage, narrative control, and managed instability).
Phase 12 argues that a Sovereign Alliance forms when multiple major powers conclude, independently or in coordination, that the supranational system is no longer tolerable, and that the only way to defeat it is to align sovereign interests across traditional rivalry lines.
What the “Sovereign Alliance” Is (In Operational Terms)
The Sovereign Alliance is not a treaty. It is not a press conference. It is an alignment of objectives - sometimes visible, sometimes deniable - designed to achieve three effects:
Break supranational leverage over national governments
Reduce the ability of global networks to trigger endless wars
Expose the parasite architecture to the populations living under it
This alliance is defined less by “friendship” than by converging incentives:
sovereignty restoration
internal anti-corruption
de-risking from captured institutions
and reducing external dependency chains (security, finance, energy, information)
Why It’s Forming (Game Theory)
In this model, the supranational system has two primary engines:
Endless war incentives (military-industrial profit, controlled destabilization, permanent emergency justification), and
Extraction incentives (debt, NGO pipelines, captured policy, and narrative enforcement).
When a nation attempts to exit that system, it is usually met with:
internal sabotage
color-revolution style destabilization
intelligence-liaison pressure
economic coercion
narrative delegitimization
and, when necessary, kinetic provocation
A Sovereign Alliance forms when multiple nations assess that they are each fighting the same internal parasite - different flags, same mechanism and that coordinated pressure is the only way to prevent being isolated and destroyed one-by-one.
What It Changes: Allies vs. Alignment
Phase 12 is where the public is forced to confront an uncomfortable reframe:
“Strongest allies” can function as the most efficient parasites.
In a captured order, the “ally” label can become a mechanism of:
policy leverage
resource extraction
foreign entanglement
intelligence penetration
and forced alignment against national interest
This model predicts that as the Sovereign Alliance reveals itself, the populations of allied countries will experience a shock event: the realization that a system framed as “security” often operated as exploitation.
The strategic purpose of that shock is not humiliation, it is liberation:
exposure → awareness
awareness → internal resistance
resistance → sovereignty reclamation
NATO, the UN, and the EU as Capture Architecture in This Model
Phase 12 places NATO/UN/EU inside a broader framework: supranational structures can be used as:
legitimate coordination mechanisms or
instruments of managed dependency
This model treats them as capture-capable systems whose incentives can drift toward:
permanent conflict management instead of resolution
bureaucratic self-preservation
narrative enforcement against dissenting populations
and policy compulsion under the banner of unity
Recent reporting illustrates a key inflection point in this arena: U.S. officials have reportedly pressed European allies to assume the bulk of NATO’s conventional defense capabilities by 2027, with warnings that the U.S. could reduce participation in certain NATO defense coordination mechanisms if the deadline is not met. (Reuters)
In this model, that timeline pressure is interpreted as a signal of strategic restructuring: forcing Europe to stand on its own, while the United States reorients toward its core national priorities.
The Western Hemisphere Doctrine: The Primary Mission Reset
Phase 12 asserts that America’s primary mission returns to the Western Hemisphere -not as isolation, but as sovereignty consolidation:
border integrity
cartel disruption
energy security and trade corridors
protection of hemispheric infrastructure
denial of foreign capture through debt and proxy networks
In this model, the sequence matters:
secure domestic legitimacy and enforcement (Phases 10–11)
then consolidate the hemisphere
then leverage that stability to withstand the external counterattacks that come with revealing the alliance
The Sovereign Alliance Hypothesis: Who the Nodes Appear to Be
This phase frames a working hypothesis: a sovereign bloc coalesces around key power centers whose interests converge against supranational capture.
The hypothesized nodes in this model include:
President Trump
President Putin
President Xi (Not the CCP)
and select Middle East leadership, particularly Mohammed bin Salman (MBS) as part of a regional stabilization and anti-chaos strategy
The claim is not that these actors “agree on everything.” The claim is that they converge on one decisive point:
the endless-war, supranational extraction order must be broken.
The Shadow War Lens: One Parasite, Many Flags
Phase 12 introduces the “two-layer conflict” concept:
The visible layer: nation-states, diplomacy, trade, and public rivalries
The hidden layer: internal capture systems that steer policy against the interests of the population
In this model, each major power has an internal adversary layer, an entrenched apparatus (Deep State) that benefits from:
corruption
foreign leverage
dependency chains
and destabilization as a tool of control
Phase 12 treats the Sovereign Alliance as an attempt to coordinate sovereign leadership against that internal adversary layer across multiple nations.
Operation Gladio as a Historical Template for Managed Instability
This phase uses Operation Gladio as a reference point - not as a slogan, but as a historical case study in clandestine “stay-behind” networks and the controversy surrounding covert influence operations in Cold War Europe. Italian Prime Minister Giulio Andreotti publicly confirmed the existence of Italy’s stay-behind network (Gladio) in 1990, and scholarly archives document the broader stay-behind context and debates about purpose and misuse. (Phpisn)
In this model, “Gladio” becomes shorthand for a strategic doctrine:
create controlled instability
shape public psychology through fear
justify expanded security power
and steer political outcomes through clandestine influence
Phase 12 positions the current period as a reversal of that doctrine: the same covert architecture that once managed instability becomes the target of exposure and disruption.
War Model Shift: Ending Forever Wars Through Compressed Operations
A core Phase 12 assertion is that the old order requires long wars to sustain:
profit
dependency
and permanent emergency narratives
The counter-model seeks short, decisive operations aimed at capability denial and deterrence, minimizing occupation and limiting the time window the adversary can weaponize the narrative.
Recent reporting on the U.S. capture of Nicolás Maduro illustrates the kind of high-impact, high-speed operation this model points to: Reuters described months of planning involving the Pentagon and CIA, special forces execution, and Maduro’s surrender inside a safe house. (Reuters)
Separately, public reporting around U.S. operations targeting the Houthis in 2025 reflects how limited-duration campaigns are framed by different actors as either deterrence or escalation, reinforcing how modern conflicts are fought simultaneously on the kinetic and narrative planes. (PBS)
In this model, the Sovereign Alliance uses compressed operations to deny the adversary its primary resource: time…time to entrench, to launder narratives, to trigger proxy wars, and to manufacture consent.
What to Watch For: Alliance Signals Without Announcements
Phase 12 trains the reader to recognize alliance formation without needing a formal declaration:
synchronized policy pivots across multiple nations
simultaneous anti-corruption moves and purges
mirrored narratives about sovereignty, borders, and internal capture
coordinated pressure on NGOs, financial channels, and intel cutout networks
rapid operations that neutralize escalatory nodes without occupation
The alliance reveals itself through patterns, not proclamations.
The Counterattack: Predictable Smear Templates
When Phase 12 activates, the information war intensifies. Expect narrative weapons designed to stop sovereignty realignment:
“treason”
“authoritarian alliance”
“end of democracy”
“isolationism”
“world war provocation”
“dangerous extremists”
The purpose of these labels is not analysis. It is deterrence, to make populations fear sovereignty more than subjugation.
Phase 12 End State
Phase 12 is complete when:
the old “ally/enemy” framework “Old Guard” collapses under evidence of exploitation
supranational capture structures are publicly legible
hemispheric consolidation reduces external leverage over U.S. sovereignty
sovereign-aligned leaders coordinate deterrence and disruption
and populations in multiple countries begin reclaiming sovereignty against internal capture systems
This phase does not end the war. It reveals the battlefield.
Bridge to Phase 13
When supranational capture begins collapsing, the adversary shifts to its most desperate tool: internal fracture…civil conflict triggers, religious-war triggers, and terror narratives intended to force populations back into fear and dependency.
That is the next phase.
Next: Phase 13 - Counter-Insurgency at Home: Shutting Down Civil War, Religious War, and Terror Triggers
Phase 13: Counter-Insurgency at Home
Shutting Down Civil War, Religious War, and Terror Triggers Before They Ignite
Phase 13 is the internal-stabilization phase. When narrative control erodes, exposure operations expand, and legal pressure begins to form a noose around entrenched power networks, the adversary’s most reliable escape route is not persuasion…it’s internal fracture.
In Fifth Generation Warfare, the goal is to make a nation turn inward until it cannot govern itself. The method is consistent across theaters and decades: manufacture fear, provoke retaliation, amplify disorder, then offer “security” as the price of surrender. This is the logic behind the “strategy of tension” - using violence and chaos to reshape public behavior and political outcomes. (Fox News)
Phase 13 exists to deny that outcome. It is the phase where the operation must prevent the adversary from forcing a domestic crisis event big enough to stop the campaign, disrupt accountability, or justify emergency governance.
Full Episode Here: COUNTER INSURGENCY with GENERAL FLYNN - PART 2
We are currently engaged in a battle by those who want to undermine President @realDonaldTrump’s agenda, but he is assembling a strong team. However, execution can only commence once he is officially in office.
Click the link below to watch Counter Insurgency Pt 2 with @xAlphaWarriorx and @realjoshuareid
Strategic Objective
To prevent escalation into mass unrest, sectarian conflict, or terror-driven emergency authorities by:
identifying and neutralizing provocation patterns early
hardening community resilience against manipulation
aligning law enforcement, intelligence, and civic leadership around disciplined interdiction
preventing the information environment from becoming an accelerant for violence
maintaining legitimacy and rule-of-law standards while pressure intensifies
This phase is not about winning debates. It is about keeping the nation stable enough for the larger operation to complete.
The Three Trigger Lanes
1) Civil War Triggers
Designed to produce clashes, retaliation spirals, and the illusion of a grassroots “national rupture.” The target is cohesion.
2) Religious War Triggers
Designed to weaponize identity, sacred grievance, and moral absolutism, until the population cannot share a civil framework. The target is moral legitimacy.
This is where extremists become tools: they are used as matchheads to ignite larger groups who never wanted conflict in the first place.
3) Terror Triggers
Designed to generate shock events that force institutions and citizens into fear compliance -surveillance expansion, censorship, emergency powers, and rapid centralization. The target is governance under panic.
Real-Time Proof: Interdiction Before Ignition
Phase 13 is not theoretical. It is demonstrated by disruption, plots stopped before they become kinetic.
Example A: ISIS-Inspired New Year’s Eve Plot Disrupted (North Carolina)
On January 2, 2026, DOJ announced the disruption of an alleged ISIS-inspired plan for a New Year’s Eve attack in Mint Hill, North Carolina. The accused was charged with attempting to provide material support to ISIS; authorities said the planned method involved knives and hammers targeting public locations. The case was described as a collaboration across federal and local partners, and the disruption was explicitly framed as preventing loss of life. (Department of Justice)
This matters operationally: it is a clear example of a terror trigger attempt neutralized before it could become a national accelerant.
Example B: New Year’s Eve Bombing Plot Disrupted (Southern California)
On December 15, 2025, DOJ announced four arrests tied to an alleged plot involving improvised explosive devices intended for New Year’s Eve attacks on multiple targets in California, with additional targeting planned against federal officers. (Department of Justice)
On December 23, 2025, DOJ announced the grand jury returned terrorism-related charges connected to that same alleged New Year’s Eve bombing plot. (Department of Justice)
Operationally, this shows the Phase 13 principle in action: deny the spectacle before the adversary can turn it into a mass-psychology event.
The Religious-War Frame: Selective Outrage as a Weapon
In this model, one of the adversary’s most effective plays is selective threat framing, pushing the public to obsess over one category of extremism while downplaying another, not to protect the public, but to keep society permanently divided.
The theory being advanced here is that engineered sectarian friction is being driven by provocateurs and extremists, pitting Christians (including Catholics), Jews, and other groups against each other to generate a domestic religious rupture. The trap is not disagreement; the trap is dehumanization + retaliation.
At the same time, Phase 13 highlights the reality that jihadist-inspired radicalization is still an active threat vector (as shown by recent cases), even when some information actors try to minimize or redirect attention away from it. (Department of Justice)
Important boundary: recognizing extremist threat vectors is not a license for collective blame. Extremism is the target, violent ideology and operational networks, not peaceful citizens.
Counter-Insurgency Doctrine: Flynn’s Core Contribution to the Model
Phase 13 is a counter-insurgency phase - domestic, informational, psychological, and operational.
A key doctrinal anchor for this section is General Michael Flynn’s and Boone Cutler’s counterinsurgency-era intelligence argument: that intelligence must stop chasing only enemy cells and instead understand the population, environment, networks, and influence pathways that insurgents exploit.
In Fixing Intel: A Blueprint for Making Intelligence Relevant in Afghanistan (2010), Flynn and co-authors argued that intelligence support to counterinsurgency was failing because it over-focused on insurgent groups while remaining unable to answer basic questions about the people and environment being contested and they called for a process that moves relevant information from sensors to decision-makers, rather than letting media narratives drive strategy. (CNAS)
That doctrine maps cleanly into the Phase 13 mission set:
Identify the networks that manufacture outrage.
Understand who benefits from escalation.
Track influence pathways, not just “bad actors.”
Deny insurgent-style provocation cycles by staying disciplined, evidence-based, and psychologically resilient.
Counterinsurgency is not only kinetic. In 5GW, it is fought through perception management, social cohesion, and decision advantage.
OPSEC as a Weapon: Closing Internal Leaks and Hardening the Force
Phase 13 also requires internal discipline inside institutions.
One operational marker consistent with OPSEC hardening is active leak identification efforts. Reporting cited by a member of Congress states that, at FBI Director Kash Patel’s direction, the bureau began administering polygraph tests in leak investigations tied to potential damage to security protocols. (houlahan.house.gov)
In the Phase 13 framework, that is not a “bureaucratic detail.” It represents the battlefield reality that:
information leaks can sabotage operations
they can compromise surveillance and interdiction
they can trigger preemptive narratives that protect adversary networks
they can undermine public confidence and create operational hesitation
Regardless of one’s politics, the principle is timeless: OPSEC is the shield that allows prevention to work.
The Provocateur Pattern: How Movements Get Set Up
A central Phase 13 risk is the use of cutouts and provocateurs to push a targeted population into illegality, then use the optics to justify crackdowns.
This tactic is historically documented in conflict and political environments and is widely recognized as a method of entrapment, delegitimization, and escalation engineering. Think J6. (Department of Justice)
The operational purpose is consistent:
push a reactive minority into unlawful action
capture it, amplify it, and generalize it
fracture the broader movement into “radicals vs. traitors”
justify exceptional measures in the name of “security”
expose Social Media Operatives trying to incite Americans into violent rhetoric. The loud voices on X Spaces etc., calling for, or implying violent responses or surrendering U.S Citizenship to move to other countries.
Phase 13 denies the adversary by refusing the bait - staying lawful, disciplined, and psychologically unsteerable.
End State: No Emergency Governance Pathway
Phase 13 is complete when:
trigger attempts fail to scale
terror incidents are disrupted before ignition
sectarian escalation is denied through discipline and lawful action
provocateur operations are exposed and neutralized
institutions maintain legitimacy while accountability operations continue
This phase is not measured by the absence of tension. It is measured by the absence of ignition.
Key Takeaway
Phase 13 is about denying ignition, stopping the adversary from forcing America into a fear-driven emergency posture. When terror triggers fail, when provocateurs can’t spark retaliation spirals, and when sectarian bait no longer works, the enemy loses its final domestic leverage: the ability to govern through panic.
That is the turning point.
Because once the population refuses to fracture and the system can no longer manufacture crisis to regain control, the next phase becomes possible:
cohesion.
Next: Phase 14 - National Unity After Exposure
How shared reality is rebuilt once controlled opposition collapses and the country regains common ground.
Phase 14: National Unity After Exposure
Unity Earned…Not Declared
Phase 14 is the cohesion phase, the point where exposure, legal warfare, election lock-in, and domestic stabilization converge into the most important strategic outcome of all: a population that cannot be fractured again.
In Fifth Generation Warfare, unity is not a slogan. It is a capability. A nation is sovereign only to the degree that its people can share reality, hold institutions accountable, and refuse to be emotionally steered into chaos.
Phase 14 begins only when the adversary loses its primary tools:
the ability to control the narrative
the ability to stall accountability indefinitely
the ability to hijack elections through procedural opacity
the ability to trigger civil fracture through provocation and fear
At that point, the war does not end. It changes form. The objective is no longer merely exposure, it is permanence.
The Phase 14 Trap: “Unity” Used as a Shield for the Unexposed
This phase must begin with a warning, because it is one of the most weaponized concepts in the entire operation:
Calls for unity too early can be sabotage.
A captured movement is often pressured into “unity” before it is ready, not because unity is the goal, but because early unity freezes exposure. It forces reconciliation before the public has identified the cutouts, the pretenders, and the psychological operators embedded in the ecosystem.
This premature unity is typically packaged as:
“Stop fighting each other”
“We need to come together now”
“Don’t focus on the negative”
“It’s all part of the plan”
“Just have faith…don’t question”
It is often sold as “hope,” but operationally it functions as amnesty through fatigue, a demand that the audience move on before accountability can attach.
In this doctrine:
Unity is not the starting point. Unity is the earned end state.
Division collapses only after false factions collapse.
What Unity Actually Means in This Doctrine
Phase 14 does not mean “everyone agrees.”
Phase 14 means the population becomes unsteerable.
It is the restoration of a shared baseline:
shared reality
shared threat recognition
shared commitment to lawful accountability
shared rejection of engineered civil conflict
This is how a nation becomes hard to capture again.
Americans Unite After Exposure, Not Politically, but Existentially
The unity described here is not partisan. It is existential.
It is what happens when enough citizens recognize:
the real target was sovereignty
the method was manipulation and managed division
the purpose was dependency and control
and the “sides” were often manufactured to keep the population fighting itself
When controlled opposition collapses, unity does not have to be forced. It becomes natural, because the false choices lose credibility.
Americans unite after the fakes are exposed, not as a party, not as a brand, but as a nation.
How Unity Is Rebuilt (Doctrine, Not Emotion)
1) Unity Requires a Common Enemy Definition
A fractured nation cannot unify if it cannot name what attacked it.
Phase 14 clarifies the enemy definition at the level of structure:
capture systems
transnational exploitation pipelines
narrative control mechanisms
corruption networks that profit from chaos
Unity does not require uniform ideology.
Unity requires shared recognition of the threat architecture.
2) Unity Requires Justice Without Vengeance
Accountability remains non-negotiable. But vengeance is a trap.
Phase 14 establishes a disciplined posture:
investigations remain evidence-driven
guilt remains individual, not collective
punishment remains lawful, not mob-driven
reforms remain structural, not symbolic
A nation that replaces one form of lawlessness with another becomes governable only through repression. That is not sovereignty.
3) Unity Requires a Civil Re-Legitimation Process
Once public confidence collapses, institutions cannot demand trust. They must earn it through:
transparency
measurable reform
auditable systems
consequences for violations
visible correction of past failures
Legitimacy is rebuilt as an operational capability, not a public relations campaign.
4) Unity Requires a New Information Ethic
Phase 14 codifies the discipline developed earlier into a cultural standard:
verify before amplifying
resist outrage bait
refuse dehumanization
measure claims by evidence, not tribe
treat morale as a weapon, not a mood
A population with an information ethic becomes hard to infiltrate, hard to demoralize, and nearly impossible to steer into civil conflict.
5) Unity Requires Local Bonds Stronger Than National Manipulation
Strategic fracture campaigns rely on national abstraction, turning citizens into stereotypes.
Phase 14 is rebuilt from the ground up:
community cohesion
faith communities resisting provocation
veterans and law enforcement restoring trust through legitimacy and service
civic organizations focused on shared needs instead of tribal theater
When local bonds strengthen, national-level manipulation loses power.
Morale as Strategic Dominance
Morale is not optimism. Morale is the population’s willingness to endure stress, remain disciplined, and pursue the mission without collapsing into despair or rage.
Demoralized people surrender oversight.
Demoralized people outsource decisions.
Demoralized people accept managed decline as inevitable.
Demoralized people become easy to steer.
Phase 14 treats morale as strategic dominance because morale is what keeps a nation sovereign when the enemy’s only remaining weapon is internal fracture.
Phase 14 End State
Phase 14 is complete when:
shared reality is restored enough to prevent mass manipulation
trust in institutions begins returning through auditability and reform
unity becomes resilient to infiltration and provocation
citizens can disagree politically without becoming enemies
the nation transitions from exposure-mode into rebuild-mode
At that point, the adversary’s primary weapon - fracture - no longer works at scale.
Key Takeaway
Phase 14 is where the country becomes difficult to defeat.
Not because everyone agrees.
But because the nation can no longer be steered into chaos through fear, deception, and controlled conflict.
Unity becomes the shield.
Morale becomes the weapon.
Sovereignty becomes the outcome.
Bridge to Phase 15
Once unity becomes resilient and the false factions lose oxygen, the adversary is forced into direct survival behavior…high-risk escalations, desperate operations, and final attempts to preserve remaining power nodes.
That is the threshold of the final battle.
Next: Phase 15 - The Final Battle
Mid/Late 2026 to early 2027: the last escalation attempts, the collapse of remaining power structures, and the decisive end of the captured order.
PHASE 15: The Final Battle - Shock, Chaos, and Counter-Network Control (Mid/Late 2026 to Early 2027)
Phase 15 is where an entrenched adversary - facing exposure, prosecutions, financial disruption, and collapsing narrative control - reaches for the oldest move in the playbook: manufactured disorder. When persuasion fails, panic becomes the weapon. When legitimacy collapses, sabotage, intimidation, and economic trauma become leverage.
This phase is not defined by a single event. It is defined by a portfolio of shocks -stacked fast enough that ordinary people start asking the wrong question (“Who do I blame right now?”) instead of the right question (“Who benefits from the reaction?”). The objective is not only damage. The objective is a psychological condition: demoralization, tribal fracture, and a public too exhausted to govern itself.
The modern threat environment described by U.S. government threat assessments reinforces why a “shock portfolio” is a rational adversary strategy: the Homeland faces simultaneous pressure from terrorist mobilization dynamics, state and proxy activity, and persistent cyber threats against critical infrastructure. (Director of National Intelligence)
The Game Theory of Chaos
In game-theory terms, the adversary is no longer optimizing for “winning the argument.” They are optimizing for maximizing confusion while minimizing attribution:
Overload the system: many small-to-medium crises beat one big crisis because they stretch response capacity and public attention.
Force misattribution: make events look like incompetence, “random failure,” or “both sides.”
Trigger tribal sorting: push influencers and factions into mutually exclusive narratives.
Exploit the reaction loop: fear → overreaction → optics → recruitment → escalation.
The counter-strategy is deterrence by denial: reduce the payoff of chaos. That does not require perfection; it requires turning chaos into a losing investment - fast disruption, rapid containment, disciplined messaging, and a population trained to resist provocation.
The Shock Portfolio: Four Lanes of Escalation
Phase 15 is best understood as four lanes that can run independently or synchronized.
Lane 1: Kinetic Terror and “Distributed” Attacks
The most efficient terror campaigns are often not complex…they are replicable, psychologically contagious, and low-cost. Recent disrupted plots illustrate the operational logic: online radicalization, target selection, symbolic timing, and a desire to provoke law enforcement response and mass fear. (Department of Justice)
Low-tech mass casualty attempts (knives, hammers, vehicles, improvised devices) remain attractive because they are harder to detect early than sophisticated plots. (Department of Justice)
Coordinated bombing plots, even when stopped, serve the narrative goal: “the country is ungovernable.” (Department of Justice)
Game-theory note: high “success rates” are not required. The adversary needs enough attempts to keep the population in a sustained elevated threat state.
Lane 2: Cyber Disruption and Communications Degradation
Cyber is the cleanest lever for chaos: it produces real pain while keeping attribution blurry. U.S. threat assessments and FBI testimony emphasize persistent cyber risk and the pressure it places on domestic stability and critical systems. (Director of National Intelligence)
Critical-sector targeting (including healthcare and essential services) generates slow panic, cascading service failures, and distrust in institutions. (American Hospital Association)
Narrative isolation during crisis windows can occur when communications degrade, whether by cyberattack, platform disruption, or state action; recent events in Iran underscore how quickly information flow can be constrained during unrest. (reuters.com)
Game-theory note: in Phase 15, cyber is rarely “about money.” It is about tempo control, slowing public coordination while accelerating panic.
Lane 3: Infrastructure Failures and “Accident Clustering” Narratives
One of the most effective psychological operations is turning routine risk into perceived conspiracy—or turning sabotage into perceived routine. Either way, the public loses the ability to judge reality.
In Phase 15 logic, the adversary benefits from “cluster perception”: multiple incidents in a short window create a felt sense of systemic collapse, even when events are unrelated. The counter is disciplined interpretation and verified attribution, not reflexive mass conclusion.
Lane 4: Financial Shock and Liquidity Panic
Financial chaos is the “king move” because it impacts everyone at once. The objective is not merely recession; it is a confidence break: market whiplash, banking fear, supply disruptions, and “run psychology.”
Recent fiscal reporting illustrates why revenue levers and public perceptions of economic control, matter in Phase 15. U.S. Treasury reporting shows customs duties rising sharply in FY2025 (customs duties reported at $194.9B, up substantially year-over-year), and contemporaneous reporting tracked record-level tariff receipts. (Bureau of the Fiscal Service)
Game-theory note: financial panic is contagious. The defense is not “no volatility.” The defense is credible continuity: payment rails, liquidity backstops, and public confidence that governance and essential services remain intact.
Counter-Network Architecture: Denying the Payoff of Chaos
Phase 15 defense is not a single agency; it is a layered architecture that blends federal capability, state readiness, and local continuity.
Layer 1: Harden the Perimeter and Cut Mobility
Public reporting in 2025 described a large-scale border-support posture, with the Defense Department briefing that approximately 8,500 military personnel were attached to Joint Task Force–Southern Border, and additional reporting describing deployments pushing totals near 10,000. (JBSA)
Layer 2: Rapid Containment Inside the Wire
Reporting in late 2025 described Pentagon direction for National Guard “quick reaction” forces trained for civil disturbances and readiness targets by early 2026. (reuters.com)
Layer 3: Counterterror Disruption Before Headline-Scale Events
Recent DOJ actions show the preferred defensive pattern: contain the attempt at the planning and mobilization layer rather than after execution. (Department of Justice)
The Secret Weapon of the Final Battle: Public Opinion, Perception, and Local Action
The Social Media Shadow War and the “Ghost” Layer of the Campaign
Phase 15 is not only fought with courts, interdictions, and cyber defense. It is fought in the domain that decides whether those tools can be used without being politically neutralized:
Public opinion.
Perception.
Local action.
In this analytical model, the White Hat side always understood a final truth about modern conflict: in an open society, authority is downstream from legitimacy, and legitimacy is downstream from what the public believes is real. A technically perfect operation can still be defeated if the population is psychologically broken, confused, or provoked into unlawful reaction. A legally airtight case can still be stalled if the public is manipulated into fatigue, cynicism, or internal fracture.
That is why decentralization is not treated here as a “content style,” but as a survivability requirement. It denies the adversary a single decapitation point, forces redundancy, and creates a population-level capability: distributed perception defense.
Why “Perception” Is the Center of Gravity
Phase 15 chaos attempts are designed to create one outcome above all others: a population that stops trusting its own judgment. When citizens lose confidence in discernment, they become controllable through fear-based authority, narrative dependency, tribal identity, and emergency-power consent.
The decisive weapon against that is not simply “more information.” It is disciplined perception, people trained to recognize manipulation, resist provocation, verify before amplifying, and maintain morale under shock.
The “Ghost” Layer: Distributed Influence for Stability
This model further proposes a human infrastructure layer inside the public platforms themselves - X, Facebook, TikTok, YouTube, Rumble, Substack, podcasts, comment ecosystems - operating as subtle stabilizers in the information stream.
In this framework, the Ghost layer produces three mission effects:
Stabilize perception during shock
Slow the environment down: verification discipline, source checking, refusal to amplify unconfirmed narratives, and narrative inoculation against panic.Protect the public from provocation
Neutralize bait designed to trigger unlawful reaction; identify classic manipulation templates; resist forced tribal sorting (“pick a side now”).Preserve morale without selling fantasy
Morale is a weapon, but “hopium” is a trap. The stabilization mission is steady realism: disciplined confidence under pressure.
The Most Powerful Tradecraft: Ghosts Who Don’t Know They’re Ghosts
A critical feature of this model is that an unknown portion of “Ghost” influence may remain self-perceived as fully organic. That preserves authenticity and protects operational security: fewer people believe they are “in a unit,” fewer can be targeted, flipped, or discredited as “insiders.” The effect is a resilient, decentralized layer of stabilization that is harder to map and harder to neutralize.
The Adversary Mirror: Operatives in the Same Platforms
Phase 15 assumes the adversary mirrors this architecture: planting and leveraging digital assets to produce chaos. In this model, those assets tend to cluster into predictable types:
Provocation assets (escalate anger into unlawful action)
Demoralization assets (“nothing matters,” “no accountability,” “it’s over”, “Trump betrayed MAGA”, “Q is Operation Trust 2.0”)
Tribal sorting assets (influencer wars, loyalty tests, factional fracture)
Premature unity assets (demand amnesty through fatigue before exposure concludes)
The enemy’s kinetic plan requires a population that breaks. The counter-plan requires a population trained not to break.
Follow Chase Hughes Here: NCI
Signature Management and “Ghost” as a Professional Concept
Even outside the political model above, modern military doctrine recognizes the value of operating below detection thresholds, managing physical and digital signatures. Special operations communities publicly discuss signature management needs, including digital footprint discipline and “security through obscurity.” (DefenseScoop)
In Phase 15 logic, that concept extends beyond physical terrain into the information environment: disciplined presence, low-signature coordination, and resilience under surveillance.
Indicators & Warnings Box: A Weekly Scan for Phase 15 Escalation
Multiple disrupted violent plots across regions within days, especially tied to symbolic timing. (reuters.com)
Cyber disruption paired with narrative acceleration and calls for mass street reaction. (Director of National Intelligence)
Sudden comms restriction patterns during unrest (state-imposed or otherwise). (reuters.com)
A concentrated push for tribal sorting and “pick a side now” messaging during crisis windows (Candace Owens vs TPUSA).
Financial-media messaging shifting from “volatility” to “doom inevitability,” paired with viral amplification.
Skeptic Filter: The Predictable Counter-Message During Chaos
During Phase 15, a predictable wedge message appears: “See? It was all fake. Nothing is controlled. Everything is falling apart.” That message is not proof of absence. It is an expected narrative move when the public is overwhelmed: convert chaos into fatalism.
The correct posture is this: chaos does not disprove design - chaos can be the last lever when design is losing.
Rules of Engagement: Discipline Under Shock
Do not react inside the first information wave.
Do not amplify unverified claims, images, or “insider” threads.
Track patterns, not anecdotes.
Assume provocateurs exist in every large digital crowd; treat rage as a cue to slow down.
Prioritize lawful action and continuity; the objective is stability, not “winning a moment.”
Maintain comms redundancy outside any single platform.
Refuse tribal sorting; “pick a side” pressure is often the trap.
Hold the line on morale; panic is contagious, but so is steadiness.
Bridge to Phase 16
If Phase 15 is the adversary’s last bid to fracture the public through shock, then Phase 16 is the inversion: stability, reconstruction, and legal resolution at scale. The closing move is not merely surviving chaos….it is proving, in courts and governance, that chaos failed to break the republic.
PHASE 16 Strategy Blueprint
Global Sovereignty and Trials: Rebuilding Legitimate Governance After the Collapse of the Captured System
Phase 16 is the conversion phase: converting exposure (Phase 1–15) into durable governance, lawful accountability, and non-reversible sovereignty. If Phase 15 is “survive the shock portfolio,” Phase 16 is “lock the win into institutions so it can’t be reversed.”
Phase 16 operates as a whole-of-system stabilization and justice campaign with four simultaneous objectives:
Stabilize society (deny vacuum, revenge cycles, and counter-coups)
Formalize accountability (enterprise mapping, trials, asset recovery)
Rebuild legitimacy (auditable elections, courts, media, finance)
Rebuild culture (restoring cohesion and meaning structures)
1) Commander’s Intent
Intent: Restore sovereign governance and public trust while prosecuting the enterprise, without triggering civil conflict, economic collapse, or a “return of the parasite” through amnesty, delay, or infiltration.
Decisive point: The moment the public sees that justice is real, lawful, and durable - not performative, not selective, and not collapsible under pressure.
2) The 7 Lines of Effort (LOEs)
LOE 1 - Stabilization & Continuity of Government
Goal: prevent a power vacuum and keep essential services running.
Keep courts, utilities, food supply, banking rails, and local government functioning
Establish continuity protocols for disruption and sabotage attempts
Maintain strict ROE: de-escalation, lawful action, documentation, minimal force
Prioritize governability over spectacle
Game theory: If the adversary can’t win legally, they’ll try to win through exhaustion and instability. Continuity denies them payoff.
LOE 2 - Evidence Architecture & Case-Building at Scale
Goal: convert exposure into admissible cases.
Consolidate evidence into chain-of-custody disciplined repositories
Build enterprise maps: nodes, money flows, cutouts, influence pathways
Convert open-source material into court-ready exhibits via authentication
Standardize timelines across jurisdictions
Protect whistleblowers and key witnesses
Phase 16 “proof point” alignment (declassification + public record):
In July 2025, the Office of the DNI publicly released material and statements alleging that Obama-era national security leadership “manufactured and politicized” intelligence to undermine Trump after the 2016 election. (ODNI) That same window included a high-visibility White House briefing in which the press office echoed those allegations and named specific former officials. (Roll Call)
Game theory: The legal endgame requires “public belief” to be converted into “public record.” Phase 16 is where claims must survive sunlight, procedure, and court standards.
LOE 3 - Prosecution Strategy: Enterprise First, Actors Second
Goal: prosecute the system, not just individuals.
Start with enabling crimes (funding pathways, laundering, procurement fraud, influence operations, racketeering patterns)
Sequence prosecutions:
“easy wins” (clean documentation, cooperative witnesses)
mid-tier operators (cutouts, facilitators, fixers)
senior coordinators (decision nodes)
Offer narrow cooperation deals that expand enterprise visibility, not political immunity
Phase 16 “proof point” alignment (DOJ posture):
Following the DNI releases, DOJ announced a strike force to assess the disclosed material and determine next legal steps, signaling that the matter is being evaluated through formal legal mechanisms rather than remaining purely narrative warfare. (Department of Justice)
Game theory: The enterprise survives by insulating the top. Enterprise strategy flips the pyramid - pressure rises upward.
LOE 4 - Asset Recovery & Financial Re-Sovereignization
Goal: remove the fuel source and return stolen capacity.
Seize and recover assets tied to enterprise conduct (lawful forfeiture, EO13818 example)
Freeze and unwind NGO/contract laundering pipelines
Rebuild budget integrity: auditing, procurement reform, transparent disbursements
Reduce external leverage points (debt traps, dependency chains, captive institutions)
Phase 16 “proof point” alignment (follow-the-money doctrine):
Phase 16 is where “who funds unrest” shifts from rumor to audited inquiry. In October 2025 coverage of a White House Antifa-focused roundtable, investigators publicly pointed to funding ecosystems and explicitly named major donor networks, including Arabella, Tides, and Open Society - as targets of financial tracing and transparency efforts. (WBFF)
Separate White House materials from that period framed Antifa as a domestic threat and tied policy action to disrupting the infrastructure behind organized unrest. (The White House)
Game theory: If you don’t remove the money engine, the network regenerates under a new label.
LOE 5 - Institutional Surgery (Permanent Reforms)
Goal: make recapture structurally difficult.
Core reform targets:
Elections: auditable chain-of-custody, paper trails, clean rolls, transparent procedures
Intelligence: oversight hardening, compartmentation discipline, counter-leak OPSEC protocols
Law enforcement: corruption-resistant internal affairs, task force integrity, standardized evidence handling
Courts: resilience against lawfare and conflicts of interest; procedural transparency and in-line with the Constitution. Remove Unconstitutional Laws
Media/info systems: transparency of funding pathways, foreign influence exposure, auditable correction standards. Removal of Obama’s Smith-Mundt Modernization Act
Game theory: Phase 16 changes the game board, not just a single match.
LOE 6 - Narrative Legitimacy & National Reconciliation Without Amnesty
Goal: unify existentially while holding accountability.
Establish a public truth standard:
evidence over personality
verification over viral
lawful process over revenge
Communicate like an ops brief:
what’s known, what’s not, what’s next
publish milestones, not hype
Provide dignity pathways for the misled:
isolate malicious operators
allow honest citizens to rejoin without humiliation
Game theory: If reconciliation becomes amnesty, the enterprise survives. If justice becomes vengeance, instability returns. Phase 16 threads the needle.
LOE 7 - Cultural Restoration & Social Cohesion (Counter-Ideological Rebuild)
Goal: reverse long-term demoralization by restoring the cultural pillars that make a sovereign nation resilient.
This LOE treats culture as national security infrastructure. A captured society is easier to steer when it is atomized, meaning-starved, and ashamed of its inheritance. Phase 16 therefore includes deliberate cultural restoration aimed at returning America to cohesion and continuity.
Key restoration targets:
The nuclear family as the default social engine
Marriage and commitment as prestige again
A renewed desire for larger families
Faith and moral formation returning to public life (including education)
Merit and excellence replacing DEI capture incentives
Degenerate behavior no longer protected as untouchable virtue
Game theory: Culture is the long game. If LOE 7 is ignored, the enterprise returns under a new language layer within one generation.
3) International Dimension: Sovereignty by Cross-Border Enforcement
Phase 16 treats transnational criminality and regime-level protection rackets as part of the same enterprise logic, because the escape route is always “jurisdiction.”
Phase 16 “proof point” alignment (Venezuela as a live legal object):
In early January 2026, DOJ documentation and reporting describe a newly unsealed filing/indictment posture involving Nicolás Maduro and narco-terrorism-related charges - used as part of the broader legal framing around the Venezuela operation and subsequent proceedings. (Department of Justice)
Game theory: The transnational network relies on jurisdiction hopping. Coordinated sovereignty collapses escape routes.
4) Threats to Phase 16 (Anticipate the Countermoves)
Phase 16 is where the enemy tries to survive through lawfare, sabotage, and narrative poisoning:
injunction storms, venue shopping, procedural freezes
witness intimidation and evidence attacks
“unity now” campaigns designed to halt prosecutions
market fear operations to force “stability above justice”
institutional resistance and bureaucratic mutiny
Counter: continuity + evidence discipline + transparent milestones + protection of key nodes.
5) Metrics of Success
Phase 16 is working when:
essential services remain stable despite sabotage attempts
prosecutions move from symbolism to enterprise mapping
asset recovery hits enabling structures, not scapegoats
elections become auditable and boring again
public trust rises because process is visible and lawful
international nodes begin collapsing via coordinated exposure and action
cultural cohesion improves: family formation rises, community trust rises, meaning structures strengthen
6) Bridge to Phase 17
Phase 16 ends when the captured order can no longer regenerate through money, narrative, or infiltration and legitimacy is rebuilt enough that society shifts from survival into construction.
That is Phase 17: the Golden Age…not as fantasy, but as post-conflict reconstruction where sovereignty becomes normal and the public no longer lives in constant threat posture.
PHASE 17: The Golden Age - The End State, the Sustainment Plan, and “Trust the Plan” as Doctrine
Phase 17 is not a victory lap. It is the post-conflict sustainment phase, the part most revolutions fail because they confuse “defeating the enemy” with “building a durable future.” In this model, Phase 17 is the end state the earlier phases were designed to make possible: a sovereign society that is structurally difficult to capture again.
By Phase 17, the reader should not only understand what “The Plan” is, but be able to defend why “Trust the Plan” was never a slogan. It was a doctrinal posture:
trust the sequencing
trust the method
trust lawful accountability
trust disciplined perception
trust local action
trust the people’s role as the permanent shield
Phase 17 converts that posture into a long-term operating system.
1) Commander’s Intent (Golden Age)
Intent: Consolidate sovereignty, restore legitimacy, rebuild culture, and achieve a generational lock so capture cannot regenerate under new branding.
Decisive point: When the nation no longer requires constant crisis awareness to stay free, because systems are auditable, institutions are trustworthy, and culture is resilient.
2) The Golden Age End State: Five Pillars
Pillar 1: Legitimate Governance (Trust Rebuilt Through Auditability)
Phase 17 governance is defined by verification:
elections become auditable and boring
budgets become readable and trackable
agencies become accountable and measurable
oversight becomes routine, not scandal-driven
Trust the Plan in Phase 17 means: trust the system because it can be checked.
Pillar 2: Justice Institutionalized (Not Performative)
Phase 17 justice is not a spike of prosecutions; it is a permanent deterrent architecture:
enterprise prosecution playbooks become standard
corruption pathways are structurally blocked
consequences for abuse become normal
whistleblowers are protected by law and culture
Trust the Plan means: justice becomes the rule, not the exception.
Pillar 3: Sovereignty as Policy (National and Global)
Phase 17 ends the era of managed decline through dependency:
homeland and hemisphere first
foreign entanglement becomes exceptional, not default
alliances are based on reciprocity and sovereignty
laundering/trafficking networks face permanent pressure
Trust the Plan means: sovereignty becomes baseline policy.
Pillar 4: Cultural Renewal (Family, Faith, Meaning, and Standards)
Phase 17 recognizes culture as national security:
the nuclear family becomes prestigious again
marriage endurance becomes normal
family growth becomes supported, not penalized
faith and moral formation return as legitimate public foundations
merit replaces ideological capture incentives
destructive behavior is no longer protected as untouchable virtue
Trust the Plan means: meaning is restored so manipulation loses power.
Pillar 5: The People as a Permanent Shield (Civic Preparedness)
Phase 17 institutionalizes the Phase 2–15 capability:
verification habits become cultural norms
communities maintain resilience networks
propaganda templates are recognized early
provocations fail to ignite
local action remains the backbone of national stability
Trust the Plan means: the public stays trained, not hypnotized.
3) The Sustainment Plan: How the Win Is Kept
A) “Never Again” Structural Reforms
audits and transparency systems stay active permanently
procurement and NGO pipelines remain traceable and/or removed
intelligence oversight remains hardened and measurable
election integrity becomes a constitutional-level priority
B) Civic Muscle Memory
schools teach constitutional literacy and civic duty
communities normalize service, discipline, and responsibility
media consumers demand sourcing standards by default
truth becomes a culture, not a trend
C) Anti-Recapture Counterintelligence Posture
infiltration is treated as a normal threat, not a rare surprise
influence operations are exposed quickly
controlled opposition templates are recognized and neutralized
crisis events are met with disciplined verification, not panic
4) What “Trust the Plan” Means at the End
In Phase 17, “Trust the Plan” is not passive. It is active.
It means:
trust sequencing over spectacle
trust evidence over emotion
trust law over vengeance
trust discipline over panic
trust local action over online rage
trust the method that made freedom durable
The Plan was never “someone will save you.”
The Plan was always: teach the people to save the republic.
5) Metrics of the Golden Age (Proof of Arrival)
Phase 17 is real when:
elections are boring and verifiable
institutions punish corruption without partisan permission
public trust rises because systems are auditable
family formation strengthens and communities stabilize
the economy rewards work, production, and responsibility
foreign policy becomes sovereignty-first and war becomes exceptional
panic narratives stop working at scale
6) Final Doctrine: The Republic as a Living System
The Golden Age is not perfection. It is resilience. It is a society that can absorb shocks without being captured, frightened into surrender, or manipulated into hating itself.
What began as an information war ends as a restored civic identity:
A people who can see clearly.
A government that can be audited.
A justice system that can act.
A culture that can endure.
And when the next operation comes, as it always will, the nation will meet it with the one thing the parasite cannot defeat:
A population that will not be provoked, will not be divided, and will not forget.
My Final Thoughts…
If this model is correct, then the Plan’s true achievement was not simply the exposure of corruption. It was the rebuilding of a capability long suppressed in modern populations.
Trust the Plan…because the Plan was never a man.
The Plan was the method.
The Plan was the awakening.
The Plan was you.
End Note
Thank you for reading. If this framework helped you see the battlefield more clearly, please subscribe so you don’t miss the next phases of analysis, and share this worldwide, not as a “viral post,” but as a training document.
The mission is simple:
Wake up. Learn the doctrine. Hold the line. Teach others.



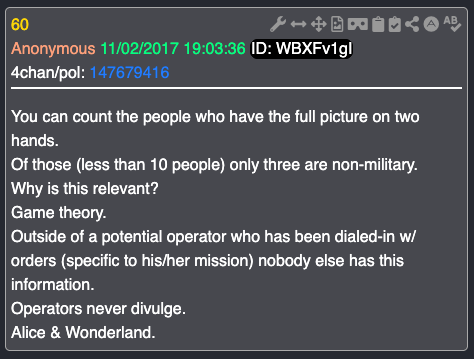
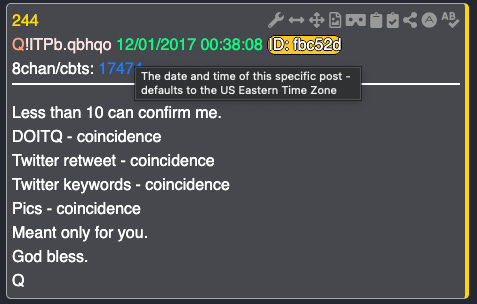
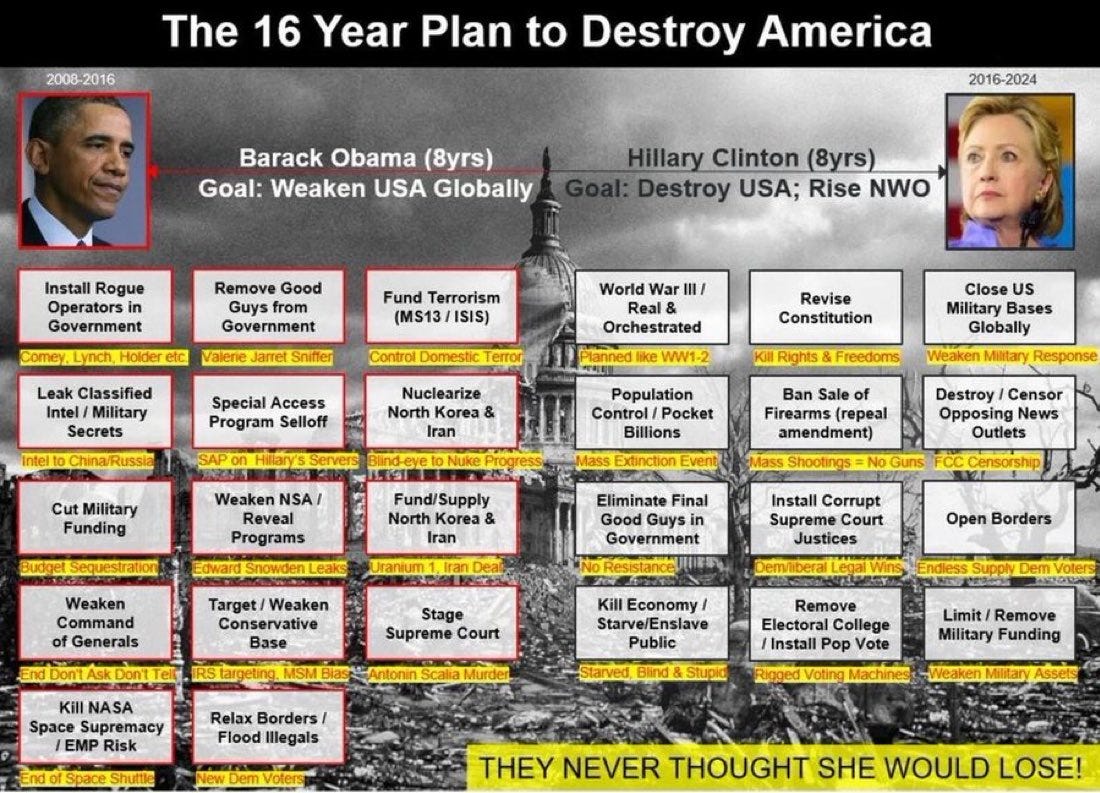
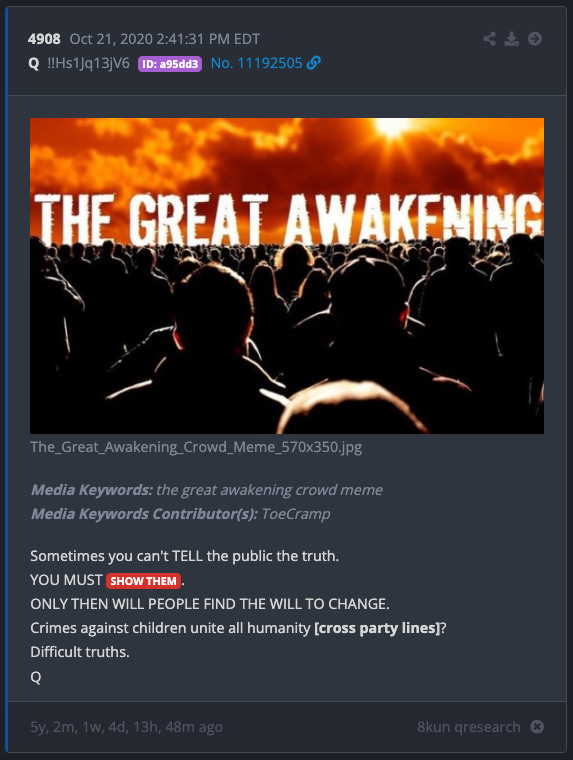
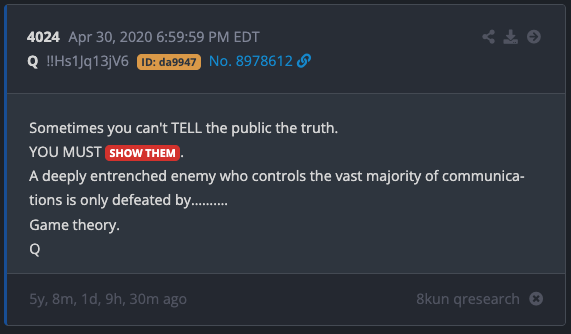


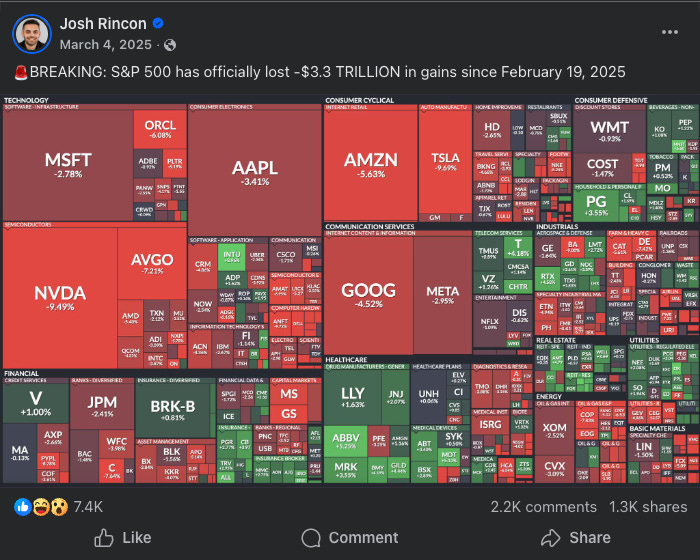


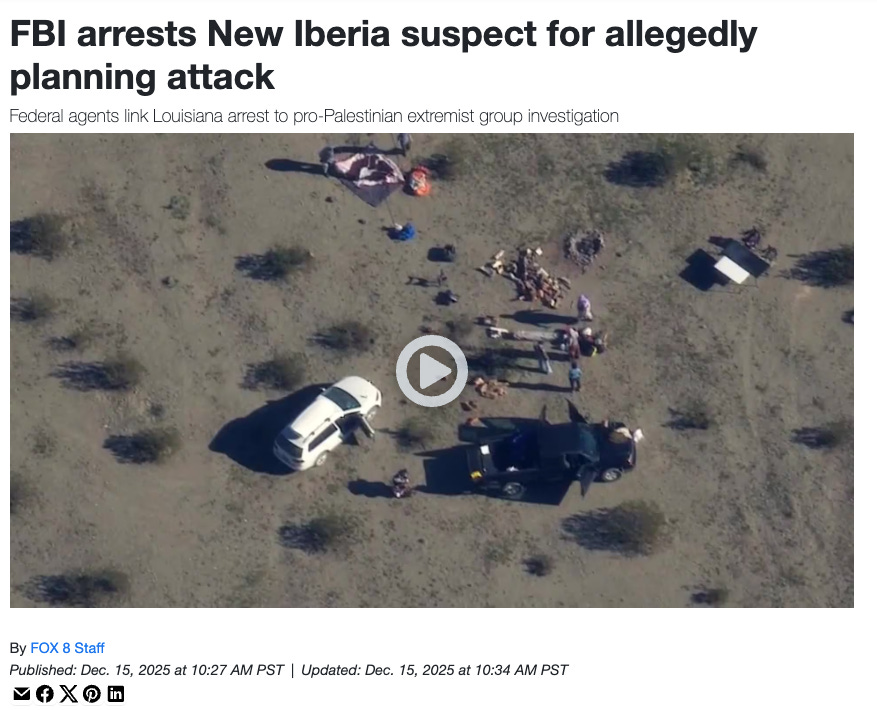
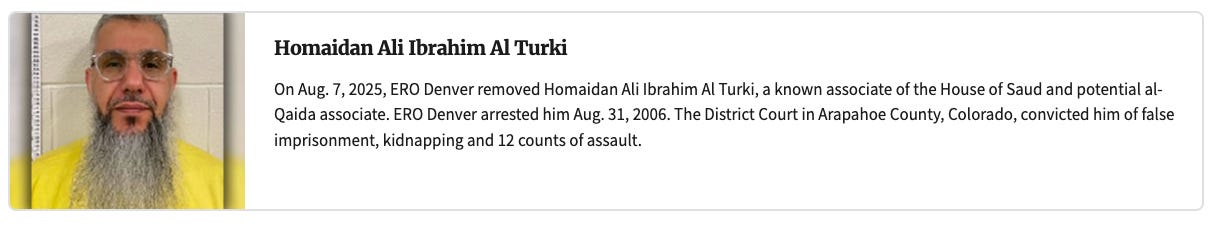
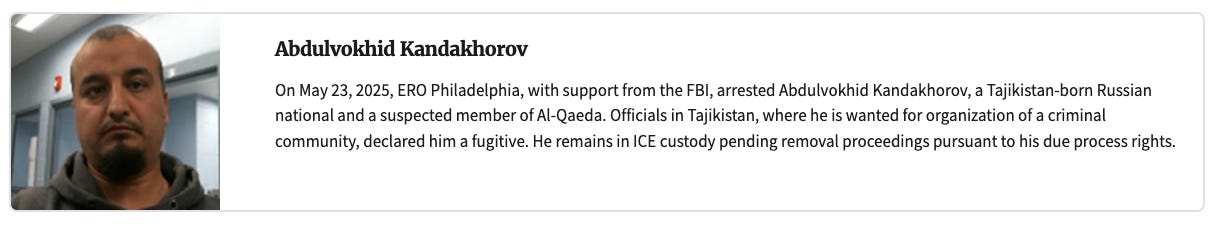

Thank you Alpha. I'd really like to have this in a book form. You are so important to this movement. Your experience and skills have made navigating this war easier to get through. Keep fighting so we can. ❣️
Wow! Someone showed Alpha THE PLAN BOOK! This analysis is excellent, and so well written for understanding. I am sharing. This should be required reading for all. Thank you so much.